|
|
Security
Planning the Pooling Security (IOM Bridge only)
Note: For SAS Integration Technologies 9.1, you can only set up pooling for SAS Workspace Servers.
For an overview of pooling, see Overview of Pooling.
For a scenario that shows how to set up pool security, see Scenario: Security Configuration for Pooling.
Overview of Pool and Puddle Configuration
To configure a pooled logical server, you must use SAS Management Console to set up one or more puddles for the pool. A puddle consists of the servers within the
pooled logical server and the puddle's pooling parameters.
To configure each puddle's security, you specify:
- a puddle login definition that is used to connect to the SAS IOM server.
Because each puddle can have only one login definition, you must define a puddle for each domain that needs
to access the pool. When you define a login definition for the puddle, the user or group metadata identity that is associated with the
login definition also has access to the puddle.
- a group metadata identity whose members (user metadata identities or other group metadata identities with associated login definitions) can also access the puddle (optional).
The login definitions associated with the group (and users that are members of the group)
are not required to have the same authentication domain as the servers in the puddle.
In addition, you must set up a user metadata identity who will be the pool administrator (used
in the Windows Object Manager metadata configuration file) and enable him or her to
view all the puddle login(s) definitions for the pool. (No other users need to be able to view these login definitions).
The following table summarizes the credentials that are required for pooling security configuration:
| Locations Where Credentials Are Specified for Pooling |
|---|
| User ID or Login Definition |
Location Where Credentials Are Specified |
Description |
Requirements |
| user ID in the spawner's metadata configuration file |
In the metadata configuration file
Note: For an Advanced or Personal installation (using SAS Configuration Wizard), the metadata configuration file named OMRConfig.xml (located in the ObjectSpawner directory) contains the SAS Trusted User credentials. |
The credentials that the spawner uses to access the metadata server. |
The user ID that you specify must be able to access metadata for the operator login (ID) and if specified, the multi-user login definition.
Note: Do not specify an unrestricted user for the user ID in the metadata configuration file. |
| operator login for spawners (optional) |
In the SAS Management Console spawner definition:
Initialization: Operator Login
 Operator Login Operator Login
Note: For an Advanced or Personal installation (using SAS Configuration Wizard), the operator login is not specified by default.
|
The Administrator login definition to access the operator port of the spawner. |
The login definition must be one of the following:
|
| login for pool administrator |
Supplied by the client application
and
In the SAS Management Console login definition
Note: For an Advanced or Personal installation (using SAS Configuration Wizard), the pool administrator login is the login for the SAS Trusted User (sastrust). You must add the default authentication domain (for example, DefaultAuth) to the sastrust login definition for pooling to function properly.
|
The Administrator login (credentials) supplied by the application to connect to the SAS Metadata Server and read the puddle login definitions. |
The login defintion must enable access to the puddle login definitions on the metadata server. |
| puddle login |
In the SAS Management Console pooled logical server definition:
Pooling  Puddles Puddles  Login Login
Note: For an Advanced or Personal installation (using SAS Configuration Wizard), the puddle login is the group login of the SAS General Servers group.
|
The login definition that is used to establish the server connection for this puddle. |
none |
| logins for users in the group that is given access to the puddle |
In the SAS Management Console pooled logical server definition:
Pooling  Puddles Puddles 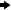 Grant Access to Group Grant Access to Group |
Logins for users in a SAS group that is granted access to a puddle. |
none |
Planning the Pool and Puddle Security
On the SAS Metadata Server, you must configure the puddle login definitions such that the pool administrator can access
all of the puddle login definitions in the pool. In addition, you must restrict who
can update the user metadata identities who are members of the group metadata identity that is granted access to each puddle,
You must also restrict who can access data on the server.
To plan for appropriate pooling security, follow these steps:
For each puddle, plan for the puddle login definition and the group metadata identity for the puddle administrator group.
To set up puddle login definitions for each puddle, you must
enable the pool administrator to view all of
the puddle login definitions for the pool. For details about which user IDs can view other login definitions,
see Enabling the User ID in the Spawner's Metadata Configuration File to View Spawner/Server Login Definitions.
To set up a puddle login definition and pool administrator for a puddle,
plan to implement the following SAS login definition, user, and group structure:
- A group metadata identity that has the puddle login definition as the group (shared) login definition
- Depending on which user ID is used for the pool administrator,
a pool administrator that is set up as follows:
Important Note: DO NOT set up an unrestricted user as the pool administrator.
- If the pool administrator's user ID is the same user ID as the puddle login definition's user ID, no additional
user and group setup is required.
- If the pool administrator's user ID is not the puddle login's user ID, set up a user metadata identity for the pool administrator.
Add this user as a member of the group (from Step a) that contains the puddle login definition as the group (shared) login definition.
(You can also create a group metadata identity for a group of pool administrators and add that group
to the group that contains the puddle login definition as the group (shared) login).
For example, the following screen shots show the Puddle1Logins group with a group (shared) login as the puddle login for Puddle 1 and the PoolAdmin user as a member of the group:
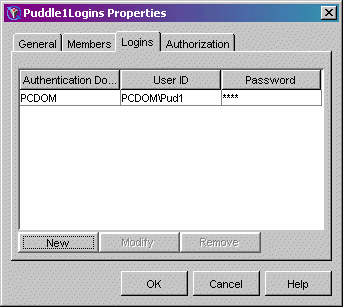
For each puddle, implement the previously described user, group and login definition structure on the SAS Metadata Server. For each puddle, plan for the group metadata identity and members (user metadata identities) of the group that are granted access to the puddle. You must
set up the group of users that are granted access to the puddle.
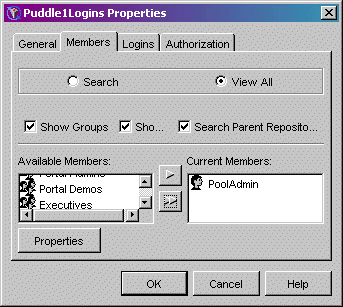
For example, the following screen shot shows the Puddle1Access group with the members (users Joe and Mark)
who can access Puddle 1:
- For each puddle, plan to control access to the group metadata identity that is granted access to the puddle. You must control access for who is authorized to
update the group metadata identity that is granted access to each puddle.
To control who can update the group metadata identity that is granted access to the puddle, in SAS Management
Console, after you set up the group metadata identity, use the Authorization
tab for the group to do both of the following:
- Deny "WriteMetadata" permission to the Public group.
- Grant "WriteMetadata" permission to your metadata administrator.
- Plan to control access to the pooled logical server.
You must control access for who is authorized to
update the pooled logical server. To control who can update the pooled logical server,
in SAS Management Console, you must use the Authorization
tab for the pooled logical server to do both of the following:
- Deny "WriteMetadata" permission to the Public group.
- Grant "WriteMetadata" permission to your metadata administrator.
- For each puddle, plan to control access to the data on the servers.
For each server you must control
access to the data on the server, either through authorization (access control) metadata
(see the Authorization Manager and User Manager plug-in help in the SAS Management Console)
or file system access on your host system.
Note: SAS Stored Process definitions are accessed under the credentials of the pool
administrator; therefore, you cannot implement access control for SAS Stored Process definitions
that are accessed by users of the puddle.
How Users Are Authenticated for the Pool
When you implement a pooled configuration, the pool administrator, the puddle login credentials, and the users who access the pool must be authenticated
against the appropriate authentication provider.
The following table shows the locations where the credentials are authenticated:
| Locations Where Credentials Are Authenticated |
|---|
| User ID Role |
Authentication Location |
| user ID of the puddle login |
host authentication provider for the SAS Workspace Server |
| user IDs of metadata identities that are members of the group metadata identity that is granted access to the pool |
SAS Metadata Server's authentication provider |
| user ID of the pool administrator credentials |
SAS Metadata Server's authentication provider |
How Users are Authorized to Access the Puddles
When users request a connection from a pool, they are authenticated
against the SAS Metadata Server's authentication provider and the pool
uses
the SAS Metadata Server to obtain the requesting user's metadata identity (user or group).
The pool then allocates a connection from the pool to the requesting user as follows:
- The pool selects a puddle where the requesting user ID matches
one of the following:
- the puddle login's user ID, or is owned by the user or group metadata identity of the puddle login's user ID.
- a user ID that is a member of the group
granted access to each puddle.
- The pool returns a connection to the selected puddle as follows:
- If a connection is available, the pool administrator returns a connection
to the requesting user. The user uses the connection as long as required.
- If there are no available connections and the maximum number of connections has not been met, the pool uses the puddle login to create a new connection.
-
If there are no available connections (to the puddle) and the maximum number of connections has been met, the requesting user waits for a connection to become available.
- When the user is finished with a connection, the user releases the connection so
it can then be used by a subsequent user.
|
 Operator Login
Operator Login


