|
|
Security
Defining Users, Groups, and Logins on the SAS Metadata Server
The User Manager plug-in of SAS Management Console provides centralized management of user
information in a SAS metadata environment.
The User Manager enables administrators to maintain user, group, and login definition information in a metadata repository.
When you register an individual user or group in the User Manager, a SAS Open Metadata Architecture metadata identity is also created for the user or group.
These definitions/identities are then used to do the following:
- authorize users or groups to access specific metadata or resources that the metadata describes.
- allow applications to retrieve appropriate login credentials for servers or other resources
Before you create the User Manager definitions, there are up to three types of domains which you must understand.
To better understand
the use of domains, refer to Overview of Domains.
The User Manager allows you to create these definitions:
-
User Metadata Identity. You can register user definitions and associate one or more login definitions with the user definition.
The login definitions are then associated with the user metadata identity and this identity is used for authorization decisions.
You can also add your user definitions to a group definition that is associated
with a group metadata identity.
The following diagram shows the relationship between a user metadata identity and its associated login definitions:
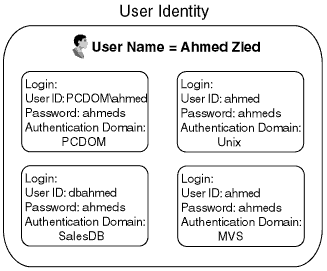
In the previous diagram, the user named Ahmed Zied contains login credentials for four different servers. These
servers are each defined in different authentication domains:
- the authentication domain that contains the server for the Windows network domain,
PCDOM
- the authentication domain that contains UNIX servers,
Unix
- the authentication domain that contains database servers,
salesdb
- the authentication domain that contains z/OS (MVS) servers,
MVS
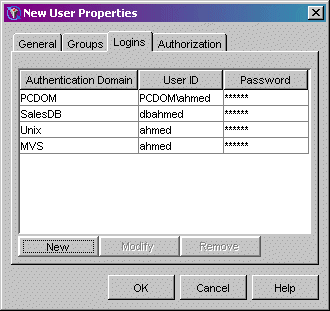
The following SAS Management Console screen shot shows the login definitions
for the user Ahmed Zied:
To define users and login definitions on the SAS Metadata Server, see
Defining a User in the SAS Management Console: User's Guide.
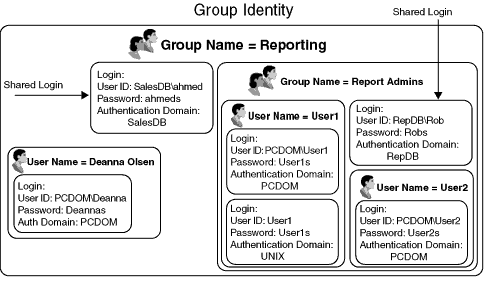
Group Metadata Identity. You can register group definitions and associate one or more user metadata identities and their login definitions with the group.
When you add user metadata identities to a group, the users and their login definitions are then also
associated with the group metadata identity. This association allows many different user metadata identities to use the same group metadata identity
for authorization.
The following diagram shows the relationship between group and user metadata identities, and their associated login definitions:
The following SAS Management Console screen shows the members of the SAS group named Reporting:
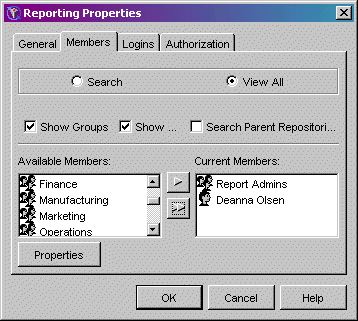
For each group, you can also define login definitions on the Logins tab of the group definition. These login definitions are then shared login definitions for the users
and other groups defined as members of the group metadata identity.
To define groups and associated login definitions on the SAS Metadata Server, see
Defining a Group in the SAS Management Console: User's Guide.
Login Definitions. A login definition contains the user credentials for a user account on a specific authentication provider. Multiple login definitions allow you to define different user credentials
for different authentication providers. These different login credentials then belong to the same user metadata identity.
For each login definition, you must define a fully qualified user ID,
password (optional), and authentication domain. For each login definition,
on the Logins tab of the user or group definition, enter the following fields as appropriate:
- Authentication Domain
The authentication domain of the login definition must match the authentication domain
of the resource you want to access with this login definition.
In the Authentication Domain field of the login definition, enter the authentication domain name that is used in the Authentication Domain
field of the resources (such as servers) that you want to access with this login definition.
Note: Applications use the name of the authentication domain that is associated with a server
to locate login definitions that contain credentials to access the server.
Choose an authentication domain name that is meaningful to the systems administrator.
For Windows users, the authentication domain name can (but is not required to) be the same as the Windows network domain name. Because applications use the authentication domain only to associate servers and login definitions, when you name the authentication domain the same as your Windows network domain, you still must enter a fully qualified user ID for the Windows system. The authentication domain is not used to construct the fully
qualified user ID.
- User ID
The user ID stored in the User ID field of a given
login definition should exactly match the host user ID. You must specify a domain in the user ID
of the login definition if you are authenticating against the following authentication providers:
- Windows host.
- Host other than Windows that is started using the AUTHPROVIDERDOMAIN option to specify a domain.
- LDAP directory server.
- Microsoft Active Directory server.
For each type of authentication provider, the following table gives information about how to specify the user ID field in a login definition:
| Format for the User ID Field in the Login Definition |
|---|
| Type of Authentication Provider Account |
Qualifier for the User ID |
Example |
Additional Information |
| Windows local account |
the name of the machine
|
If you access resources using a local Windows account that is named tara on a computer that is named mymachine.win.orionsports.com, you should have a login that includes a user ID of either mymachine\tara or tara@mymachine. |
For details about how domains are handled, see Understanding How Hosts Handle Domains. |
| Windows network account |
the name of the Windows network domain |
If you access resources using a Windows network account that is named tara in a Windows network domain that is named WINNT, you should have a login that includes a user ID or either WINNT\tara of tara@WINNT. |
For details about how domains are handled, see Understanding How Hosts Handle Domains. |
| Microsoft Active Directory account |
the name of the Windows network domain |
If you access resources using an Microsoft Active Directory account that is named tara in a Windows network domain that is named WINNT, you should have a login that includes a user ID or either WINNT\tara or tara@WINNT. |
For details, see
Specifying Authentication Providers and Domains When Starting Servers. |
| LDAP Directory account |
the name of the domain that is specified in the AUTHPROVIDERDOMAIN option when the target server is invoked |
If you access resources using an LDAP account that is named tara and the target server is invoked using
-authproviderdomain
(LDAP:Sales)
then you should have a login that includes a user ID of tara@Sales. |
For details, see
Specifying Authentication Providers and Domains When Starting Servers. |
| UNIX or z/OS account |
none
Note: If the AUTHPROVIDERDOMAIN option is used when the target server is invoked, you can qualify the user ID with the specified domain name. In most cases, this option is not specified for servers running on UNIX or z/OS. |
If you access resources using a UNIX or z/OS operating system account that is named tara, you should have a login that includes a user ID of tara.
Note: If the target server is invoked using
-authproviderdomain
(HOSTUSER:Sales)
then you should have a login that includes a user ID of either Sales\tara or tara@Sales.
|
For details about using the AUTHPROVIDERDOMAIN option, see
Specifying Authentication Providers and Domains When Starting Servers. |
| Users Authenticated via Trusted User Mechanisms |
a domain if one was passed from the Web server |
If you access resources using an account that is authenticated by a Web server's authentication
provider,
if the Web server passes credentials that contain a domain, specify a domain.
For example, WINNT\tara.
if the Web server does not pass user credentials that contain a domain, do not specify a domain. For example, tara.
|
For details, see Trusted User Connections |
| Trusted SAS Peer Sessions Authenticated via Trusted Peer Mechanisms |
If the SAS peer session connects from a Windows host, the Windows domain.
If the AUTHPROVIDERDOMAIN option associates a default domain for a SAS
peer session connection from a host other than Windows, the domain specified by AUTHPROVIDERDOMAIN
If the SAS peer connection does not connect from Windows and the AUTHPROVIDERDOMAIN option is not used to associate a default domain, no qualifier is required.
|
If the session connects from a Windows host, then you should have a login that includes a domain (for example, Sales\tara).
If the target server is invoked using
-authproviderdomain
(HOSTUSER:Sales)
then you should have a login that includes a domain (for example, tara@Sales). |
For details, see
Trusted Peer Session Connections. |
- Password
- Enter the password in the following cases:
Do not enter the password in the following cases:
Inbound login definitions: if the login definition is used ONLY as an authenticated connection to the
SAS Metadata Server in order to determine your metadata identity, a password is not required. WebDAV user's login definition for a WebDAV user that uses BASIC authentication and authenticates
against a SAS Metadata Server in the same authentication domain as the WebDAV server.
When creating login definitions do the following as appropriate:
If a user or group metadata identity has access to multiple authentication domains, create a separate Login definition for each authentication domain. If the same user ID and password combination exist in separate domains but within the same user or group metadata identity, create a separate Login definition for each domain.
Important Note: It is essential for the User Manager to resolve the fully qualified user ID to a single user or group metadata identity. For this reason,
each user ID and domain combination within the metadata server must belong to the login definition for only one user or group metadata identity.
While an identity can be associated with multiple fully qualified user IDs, each user ID and domain combination (domain qualified user ID)
must be associated with only one user or group metadata identity.
|



