|
|
Foundation Services
Understanding Events and Process Flows
The Event Broker Service configuration allows you to configure one or more events. When an event is received,
the Event Broker Service maps the event name to a configured event name. If an unstructured event is received,
the Event Broker Service maps the unstructured event to a configured default event name.
An Event configuration consists of the following information:
Additional Security Configuration
To set up security for sender's credentials or event process flows, you must
- use the User Manager plug-in to SAS Management Console to
define user or group identities in the SAS Metadata Repository.
- create, configure, and deploy the User Service (of the SAS Foundation Services).
You must configure and deploy the User Service as part of the Event Broker Service's service deployment; the User Service must be available to the Event Broker Service at run-time.
To authenticate users, the User Service requires an appropriate login module configuration file.
In addition, other Java 2 policy and JAAS policy files might be required. For example,
to run an event's process flows under a particular security context, you must set up subject-based
security with the JAAS policy configuration file in order to restrict access to the appropriate resources.
For details about required User Service configuration, see the SAS Foundation Services class documentation for the User and Security Services. For details about additional User Service configuration in the Foundation Services Manager, see Modifying the Session and User Service Configurations.
In addition, to set up authorization for sender credentials, you must grant the sender the Execute permission for the event. To grant the Execute permission:
- Use the Authorization Manager plug-in to SAS Management Console to define the Execute permission.
- From the Foundation Services Manager, open the event properties.
- On the event's Authorization tab, click Add to add the appropriate user or group for the sender.
- Also on the event's Authorization tab, select the sender's user or group identity and
grant the Execute permission.
After you define an event, you can define your process flows.
Understanding Process Flows
Process flows are used to process event messages. Process flows contain process nodes, which contain logic to process messages, and message nodes, which encapsulate the inputs and outputs for the process nodes.
- For broadcast events, you can configure one or more process flows for an event.
- For request/response events, you can only configure one process flow for an event.
You can configure a process flow by using the Process Flow Editor to define a Process Flow Diagram (PFD). A process flow configuration consists of:
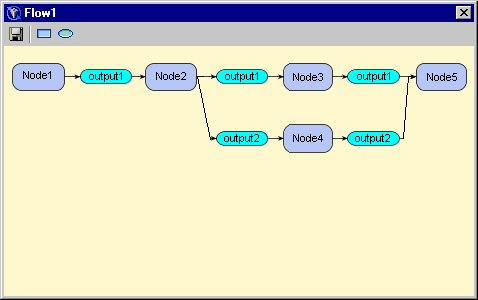
The following screen capture shows an example of a portion of a process flow diagram:
|
