The OPTNET Procedure
- Overview
-
Getting Started

-
Syntax
 Functional SummaryPROC OPTNET StatementBICONCOMP StatementCLIQUE StatementCONCOMP StatementCYCLE StatementDATA_LINKS_VAR StatementDATA_MATRIX_VAR StatementDATA_NODES_VAR StatementLINEAR_ASSIGNMENT StatementMINCOSTFLOW StatementMINCUT StatementMINSPANTREE StatementSHORTPATH StatementTRANSITIVE_CLOSURE StatementTSP Statement
Functional SummaryPROC OPTNET StatementBICONCOMP StatementCLIQUE StatementCONCOMP StatementCYCLE StatementDATA_LINKS_VAR StatementDATA_MATRIX_VAR StatementDATA_NODES_VAR StatementLINEAR_ASSIGNMENT StatementMINCOSTFLOW StatementMINCUT StatementMINSPANTREE StatementSHORTPATH StatementTRANSITIVE_CLOSURE StatementTSP Statement -
Details
 Graph Input DataMatrix Input DataNumeric LimitationsSize LimitationsBiconnected Components and Articulation PointsCliqueConnected ComponentsCycleLinear Assignment (Matching)Minimum-Cost Network FlowMinimum CutMinimum Spanning TreeShortest PathTransitive ClosureTraveling Salesman ProblemMacro VariablesODS Table Names
Graph Input DataMatrix Input DataNumeric LimitationsSize LimitationsBiconnected Components and Articulation PointsCliqueConnected ComponentsCycleLinear Assignment (Matching)Minimum-Cost Network FlowMinimum CutMinimum Spanning TreeShortest PathTransitive ClosureTraveling Salesman ProblemMacro VariablesODS Table Names -
Examples
 Articulation Points in a Terrorist NetworkCycle Detection for Kidney Donor ExchangeLinear Assignment Problem for Minimizing Swim TimesLinear Assignment Problem, Sparse Format versus Dense FormatMinimum Spanning Tree for Computer Network TopologyTransitive Closure for Identification of Circular Dependencies in a Bug Tracking SystemTraveling Salesman Tour through US Capital Cities
Articulation Points in a Terrorist NetworkCycle Detection for Kidney Donor ExchangeLinear Assignment Problem for Minimizing Swim TimesLinear Assignment Problem, Sparse Format versus Dense FormatMinimum Spanning Tree for Computer Network TopologyTransitive Closure for Identification of Circular Dependencies in a Bug Tracking SystemTraveling Salesman Tour through US Capital Cities - References
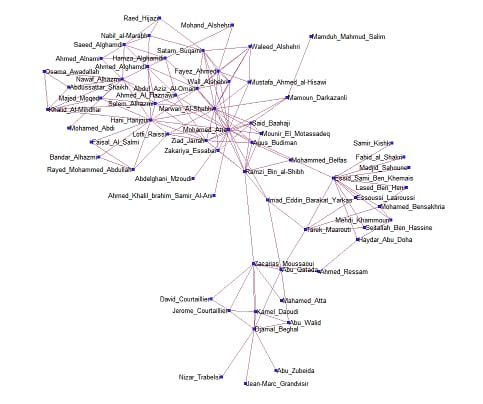
This example considers the terrorist communications network from the attacks on the United States on September 11, 2001, described in Krebs 2002. Figure 2.70 shows this network, which was constructed after the attacks, based on collected intelligence information. The image was created using SAS/GRAPH Network Visualization Workshop 2.1. See the SAS/GRAPH: Network Visualization Workshop User's Guide.
The full network data include 153 links. The following statements show a small subset to illustrate the use of the BICONCOMP statement in this context:
data LinkSetInTerror911; length from $25 to $32; input from to; datalines; Abu_Zubeida Djamal_Beghal Jean-Marc_Grandvisir Djamal_Beghal Nizar_Trabelsi Djamal_Beghal Abu_Walid Djamal_Beghal Abu_Qatada Djamal_Beghal Zacarias_Moussaoui Djamal_Beghal Jerome_Courtaillier Djamal_Beghal Kamel_Daoudi Djamal_Beghal Abu_Walid Kamel_Daoudi Abu_Walid Abu_Qatada Kamel_Daoudi Zacarias_Moussaoui Kamel_Daoudi Jerome_Courtaillier Jerome_Courtaillier Zacarias_Moussaoui Jerome_Courtaillier David_Courtaillier Zacarias_Moussaoui David_Courtaillier Zacarias_Moussaoui Ahmed_Ressam Zacarias_Moussaoui Abu_Qatada Zacarias_Moussaoui Ramzi_Bin_al-Shibh Zacarias_Moussaoui Mahamed_Atta Ahmed_Ressam Haydar_Abu_Doha Mehdi_Khammoun Haydar_Abu_Doha Essid_Sami_Ben_Khemais Haydar_Abu_Doha Mehdi_Khammoun Essid_Sami_Ben_Khemais Mehdi_Khammoun Mohamed_Bensakhria ... ;
Suppose that this communications network had been discovered before the attack on 9/11. If the investigators’ goal was to disrupt the flow of communication between different groups within the organization, then they would want to focus on the people who are articulation points in the network.
To find the articulation points, use the following statements:
proc optnet data_links = LinkSetInTerror911 out_nodes = NodeSetOut; biconcomp; run;
data ArtPoints; set NodeSetOut; where artpoint=1; run;
The data set ArtPoints contains members of the network who are articulation points. Focusing investigations on cutting off these particular members
could have caused a great deal of disruption in the terrorists’ ability to communicate when formulating the attack.