
DataFlux Data Management Studio 2.6: User Guide
DataFlux Data Management Studio supports two kinds of authentication servers: DataFlux Authentication Servers and SAS Metadata Servers. Support for SAS Metadata Servers is more limited.
SAS Metadata Servers can authenticate connections to DataFlux Data Management Servers. For example, you can use a SAS metadata identity to connect to a server on the Data Management Servers riser in DataFlux Data Management Studio. For more information about data management server connections, see Connecting to Data Management Servers. You can also specify a SAS authentication domain in a domain-enabled ODBC connection, if that connection is used in a job or profile that is executed by a data management server. For more information about these connections, see Adding Domain Enabled ODBC Connections. For more information about how SAS Metadata Servers can be used with data management servers, see Specifying an Authentication Server for a Data Management Server.
You cannot, however, use the Administration riser bar in DataFlux Data Management Studio to add a connection to a SAS Metadata Server. Also, the following servers which are often used in a data management environment still require a DataFlux Authentication Server: SAS Federation Server 3.2 and earlier, and DataFlux Web Studio 2.4 and earlier.
For more information about users and domains for SAS Metadata Servers, see SAS Management Console Guide to Users and Permissions. The rest of this topic is about DataFlux Authentication Servers only.
An Authentication Server domain is a label that is used to group similar user credentials, such as a group of users who need to log in to DataFlux Data Management Platform applications, or a group of users who need to login to a database management system (DBMS). If an Authentication Server is installed on your site, and you have administrative privilege, you can use the Administration riser in DataFlux Data Management Studio to add Authentication Server domains, users, and logins.
This topic describes the basic steps for adding domains, users, and logins on the Authentication Server. Even if you are not responsible for this task, the topic will help you understand how the Authentication Server interacts with DataFlux Data Management Studio and the Federation Server. For complete information about maintaining domains and related information, see the DataFlux Authentication Server User's Guide and the DataFlux Authentication Server Administrator's Guide.
Assume that a connection to an Authentication Server has already been added to the Administration riser, as described in Connecting to Authentication Servers.
Identify a set of domains, users, and (possibly) logins that must be registered on the Authentication Server in order to meet certain goals at your site. For example, suppose that you wanted to meet the following goals.
Goal 1: Authenticate DataFlux Data Management Platform Users. Authenticate users for DataFlux Data Management Platform applications and servers on a test computer (pubdmp). To meet this goal, you might register a domain and users such as the following.
Goal 2: Register Database Management System logins for use in job that will execute in batch mode. When a job executes in batch mode, any credentials for DBMS data sources must be provided programmatically. One solution would be to use an Authentication Server domain to retrieve DBMS credentials at run time, if the appropriate users and logins have been added to the domain. Accordingly, part of the solution for Goal 2 might be to register domains, users, and logins such as the following.

Register one or more domains on the Authentication Server, as required to meet your goals. For the example that is described in the Prerequisites section, you would create the following domains:
It is assumed that you have opened the Authentication Server as an administrator. Perform the following steps to register a domain.

In the previous figure, the Name specifies the domain name that could be combined with a login ID for authentication. The Description defines the purpose and scope of the domain. The User Name Format area specifies if and how the domain name is to be combined with a login ID for authentication. Given that the Down-level logon name option is selected in the previous figure, the domain will be combined with the login ID for authentication (PUBDMP\dfWebAdmin). The case-sensitive option is unchecked for this domain.

Register one or more users on the Authentication Server, as required to meet your goals. For the example that is described in the Prerequisites section, you would create the following users: DataFlux Admin, DataFlux User, DataFlux Web Admin, George Barnes, and Rhonda Zool.
It is assumed that you have opened the Authentication Server as an administrator. Perform the following steps to register a user.
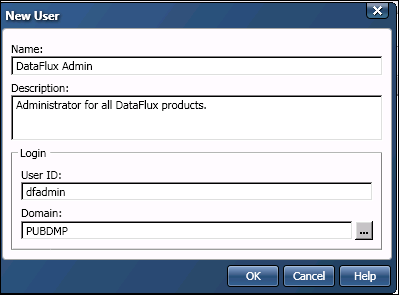
In the previous figure, the Name specifies an Authentication Server user. The Description identifies the user. The User ID specifies a login ID for this user in the selected domain. The Domain specifies an Authentication Server domain.
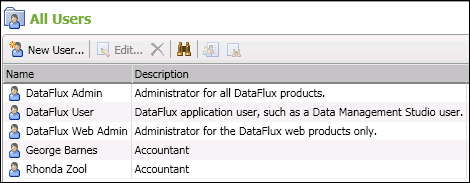
In order to meet Goal 2 as described in Prerequisites above, the DataFlux Admin user could add logins and passwords for Oracle, SQL Server, and SAP. These credentials would be retrieved at run-time by a job that is running in batch mode. For more information about this scenario, see Using Authentication Server Domains to Supply Credentials in Batch Mode.
It is assumed that you have connected to the Authentication Server and that you have opened that server on the Administration riser of DataFlux Data Management Studio. Perform the following steps to add another login to your account.

In the previous figure, User ID specifies the login ID for the target resource, such as an Oracle database. The Domain identifies the Authentication Server domain for the target resource, such as ORACLE. This domain must have already been created. The Password specifies the password for the target resource.

When a job executes in batch mode, a user cannot provide any DBMS credentials that are needed to connect to data sources. One solution would be to use an authentication server domain to retrieve DBMS credentials at run time, if the appropriate users and logins have been added to the domain. You could combine the following features:
|
Documentation Feedback: yourturn@sas.com
|
Doc ID: dfDMStd_T_AuthServer.html |