Metadata Server Tier Post-migration Tasks
Overview of Metadata Server Tier Post-migration Tasks
Running and Reviewing the Authorization Differences Reports
Overview of Running and Reviewing the Authorization Differences Reports
Impact of Migration on Access Controls
The migration process preserves all metadata layer permission
settings. However, the migration process can alter effective access
to some metadata objects. The differences in effective access are
caused by differences in access control inheritance. Access control
inheritance for a migrated object can differ from access control inheritance
for the corresponding original object for either or both of these
reasons:
-
changes in the access control inheritance rules. The rules that govern access control inheritance are slightly different in 9.2 and later than they were in 9.1. For example, in SAS 9.3 tables, cubes, libraries, and OLAP schemas inherit permissions from only their parent folders. Permissions that these objects formerly inherited through their parent application server are no longer applicable.
-
relocation of objects. The migration process relocates some objects. For example, the process moves each ungrouped library into its own folder under
SAS Folders\Shared Data. Another example is folders in custom repositories. Permissions can change for custom repository folders because in SAS 9.2 and later they become parented by the root folder of the foundation repository. When an object is moved to a new location, access to that object might change, because the object's new parent might have different settings than its old parent did.
About the Authorization Differences Reports
SAS provides reports that identify differences in access
between your SAS 9.1.3 or SAS 9.2 environment and your SAS 9.3 environment.
You should run these reports after your migration has finished. For
more information, see Run Authorization Differences Reports. Here are some key points about the
reports:
-
Each report lists objects by folder location and in alphabetical order within each folder location. For each object that has access distinctions, a separate table of changes is displayed.Note: Even if a report has a long list of objects, it is usually the case that only a few folder locations are involved. Most libraries, tables, cubes, and schemas do not have explicit settings. Instead, these objects inherit settings from their parent folders. The migration process does not add or remove permissions that have been set on these objects.
-
The reports do not reflect additional access or any changes that have been granted to the SAS Administrators group or to the SAS Administrator in a SAS 9.3 environment. This group either includes only the original SAS Administrator (sasadm) or includes both the original SAS Administrator and the members of your original SAS Administrators group.
Run Authorization Differences Reports
A good
practice is to run the authorization differences reports on the SAS
Metadata Server machine. Authorization differences reports list changes
to metadata object inheritance relationships for libraries, tables,
OLAP schema, and cubes. You manually run these reports after the SAS
Deployment Wizard has finished executing on your SAS 9.3 migrated
system.
-
Make sure that the SAS Deployment Wizard successfully extracted the authorization data from metadata.The SAS Deployment Wizard extracts authorization information for folders, libraries, tables, OLAP schemas, and cubes and stores the information in data sets before it makes changes to the metadata. The wizard names these data sets
bupxxxxxand stores them in theMetadataServer/reportsdirectory. -
Using a text editor, open SecRptAfter.sas, add metadata server connection information and the report directory path, and then save the file. This information should be on the first two lines of the file. The report directory path should be an absolute path. The following examples use common SAS configuration paths, but this path can be specific to your site. The user credentials that you specify must be for an unrestricted user. (Either the user ID is listed in adminUsers.txt with an asterisk beside it, or the user ID is a member of the Metadata Server: Unrestricted role.)Note: Depending on your operating system, the path must end with either a backslash (\, Windows) or with a forward slash (/, UNIX and z/OS).
-
Open an operating system command prompt, change directory to the reports directory, and then run the report using the appropriate SAS invocation for your operating system.On Windows and UNIX, we recommend that you run the reports using the UTF-8 encoding option. Use a non-UTF-8 execution command only when an error during extraction of the report files indicates that UTF-8 could not be used.
-
Note: On z/OS, contact the administrator for the HTTP server and request that the reports directory be available. As an alternative, you can copy the HTML and GIF files from the reports directory to another location that is already available through the HTTP server. You might want to restrict access to these reports, so consider the security of the directories to which they are copied and the audience which might access them.
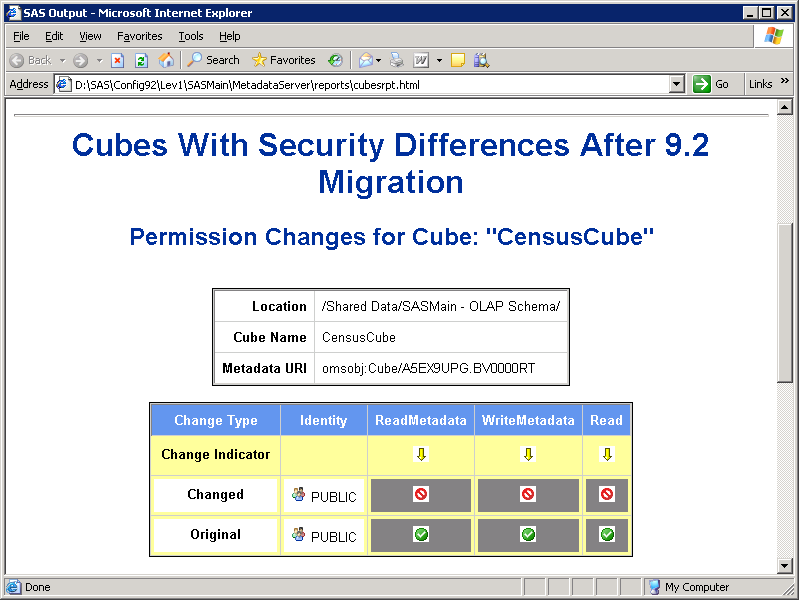
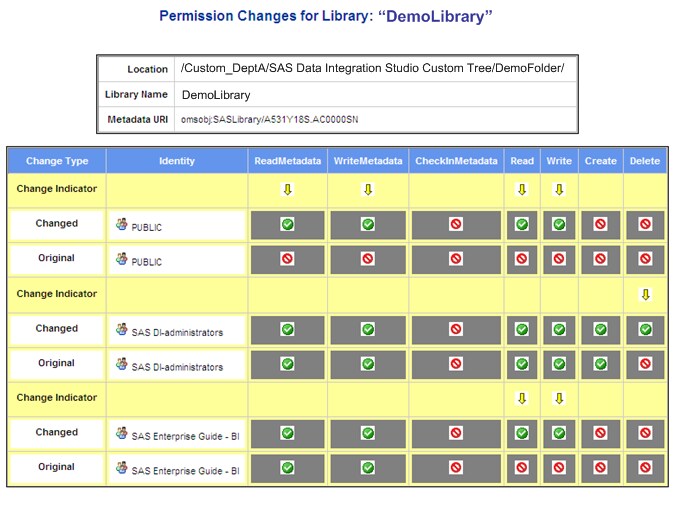
Identities Whose Access Has Changed
The
report provides basic identifying information for the DemoLibrary
and displays a list of access changes. Here are some details:
-
Note: In SAS 9.1.3, the Authorization tab does not always display effective permissions. For this reason, the settings in the Original rows in the reports might not always match the settings that are displayed in the SAS 9.1.3 Authorization tab. The SAS 9.3 Authorization tab always displays effective permissions.
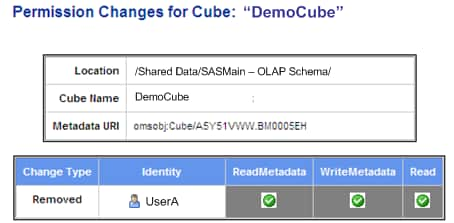
Identities Who Are Removed or Added
Causes of Authorization Differences
If you migrate an object
that derives a grant from an inheritance rule that is discontinued
in SAS 9.3, access to that object might be reduced. The following
inheritance rules are discontinued in SAS 9.3:
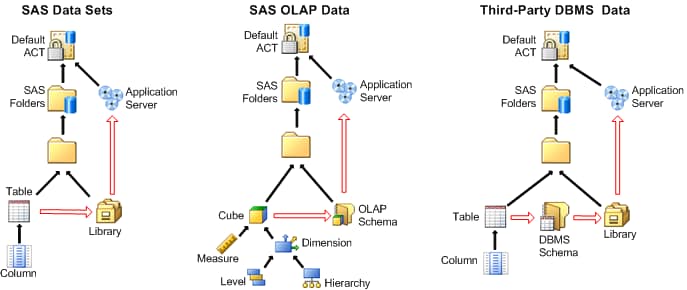
In the preceding figure,
the solid arrows indicate selected SAS 9.3 inheritance rules. The
hollow arrows indicate selected inheritance rules that existed in
SAS 9.1 but are discontinued in SAS 9.2 and later. In SAS 9.2 and
later, libraries, tables, OLAP schemas, and cubes inherit from only
their parent folders.
Note: You can use the Inheritance tab
to identify any item's parents. In SAS 9.3, you access this tab by
clicking the Advanced button on any object's Authorization tab.
The Advanced button is available to only
unrestricted users.
Addressing Authorization Differences
Your priorities influence how you address any authorization
differences that the reports identify. You might use any of these
approaches:
-
Make incremental changes to restore access to the SAS 9.1.3 state. If you have access distinctions among groups, this approach can require that you create some additional folders, set appropriate permissions on those folders, and redistribute content. For more information, see Working with SAS Folders in SAS Intelligence Platform: System Administration Guide.
Update Third-Party Software Server Definitions
Your
SAS 9.3 migrated system can contain metadata describing third-party
servers, such as Web application and database servers. These server
definitions are stored in SAS metadata repositories and might need
to be modified on the SAS 9.3 system using SAS Management Console
to reflect changes to the new system. Examples of such changes might
include new host names, ports, connection attributes, or security
information. A list of migrated third-party metadata is provided in
your SAS Migration Utility analysis report. To view your migration
analysis report, point a Web browser to the AnalysisReport.xml file
in the
AnalysisReport subdirectory
underneath the output directory you specified when you last ran the
SAS Migration Utility.