Example Use Case: Credit Card Fraud
Introduction to the Credit Card Fraud Example
This example
describes how to use SAS/GRAPH Network Visualization Workshop to investigate
patterns of credit card fraud. The data used here represent a sampling
from a large credit card transaction database. All transactions included
here, both valid and fraudulent, relate to customers with at least
one fraudulent credit card transaction.
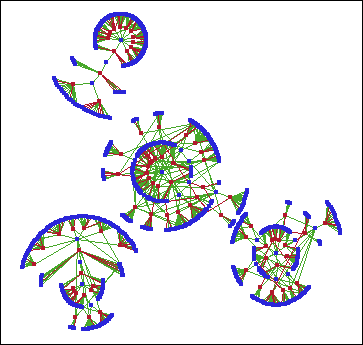
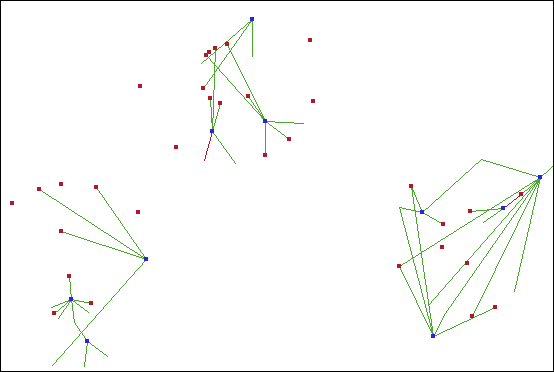
A visualization
of this data is shown in the following figure. The blue nodes in the
network correspond to merchants, and the red nodes correspond to customers.
Each link represents a transaction between a customer and a merchant.
The green links correspond to valid transactions, whereas the red
links correspond to fraudulent transactions. (Remember that all links
pertain to customers with at least one fraudulent credit card transaction
in the database.)
Open the Credit Card Fraud Project
Note: This example
describes the default settings for the ccFraudData project. If you
have made changes earlier to this project, then your settings might
differ from those described here. For example, if you have applied
a different style (other than Default), then your nodes and links
will have different colors.
About the Data Used in the Example
Determining Your Strategy
One scenario
for credit card fraud involves employees who work for the merchants
in our data sets. In this scenario, the employee steals customer credit
card numbers and either uses them or sells the numbers. The fraudulent
transaction is typically not directly associated with the merchant
where the employee works. Instead, the fraudulent transaction is connected
to another merchant through a common customer with the original merchant.
In a network graph, the fraudulent links (depicted in red here) are
typically one link removed from the problem merchant. Therefore, rather
than focus on fraudulent transactions, you will look at merchants
with a significant number of customers. Keep in mind that all customers
in the data set experienced at least one fraudulent transaction. A
merchant that has connections with many customers in the transaction
network raises suspicions of fraud. Although this approach is not
proof of fraud, it identifies specific merchants that had access to
customer credit card numbers that have fraudulent transactions associated
with them. These merchants warrant further investigation.
The degree
of a node is the number of links having that node as an endpoint.
In this example, the degree of a merchant is the number of customers
that had a transaction with the merchant. The goal, then, is to identify
merchants with high degree, which is defined here as greater than
or equal to three.
Identifying Suspicious Merchants
Examine Merchants in Group 1
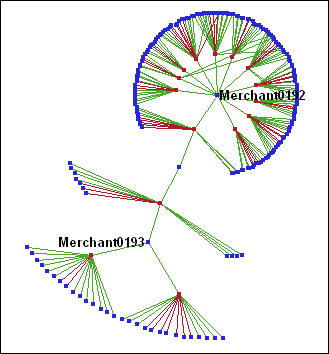
The subnetwork
in the upper left portion of the network graph contains transactions
between merchants and customers that are in Group 1. The following
figure magnifies and shows this subnetwork.
The simplicity
of this subnetwork enables you to identify the merchants with high
degree by direct observation. (Keep in mind that blue markers represent
merchants, and red markers represent customers.) When you apply labels
to the merchants with high degree, you can identify these merchants
as Merchant0192 and Merchant0193 with a degree of 11 and 3, respectively.
Examine the Remaining Merchants
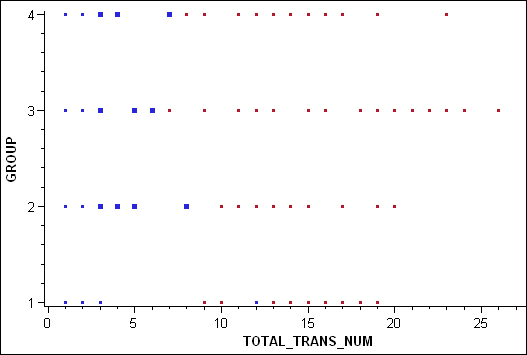
For the
remaining three clusters in the network graph, the density of the
subnetworks makes it difficult to detect all the merchants with high
degree using direct observation. You can use a statistical graph and
the local selection feature to filter the data in the network graph.
The following
figure shows the result of using a scatter plot with local selection
mode to parse the visualized data. In this graph, the blue nodes that
are visible represent all the merchants with high degree in groups
2, 3, and 4.