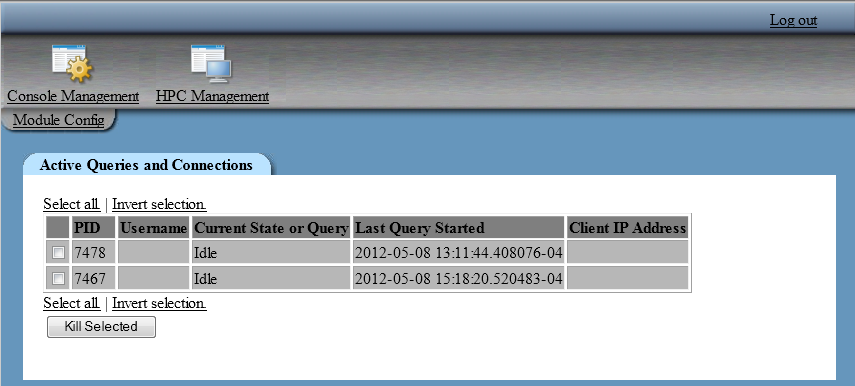
Managing Active Queries and Connections
Understanding the Active Queries and Connection Feature
For deployments that use Greenplum Data Computing Appliance
(DCA) as a co-located data provider, this feature enables an administrator
to monitor long running queries and terminate database connections.
In order to monitor
queries and terminate connections, a database user account is needed
to connect to the database with administrative privileges. In order
to list the active queries for all connections and to be able to terminate
connections, the database user account should be granted the superuser
role.
Configuring the Greenplum Database Connection
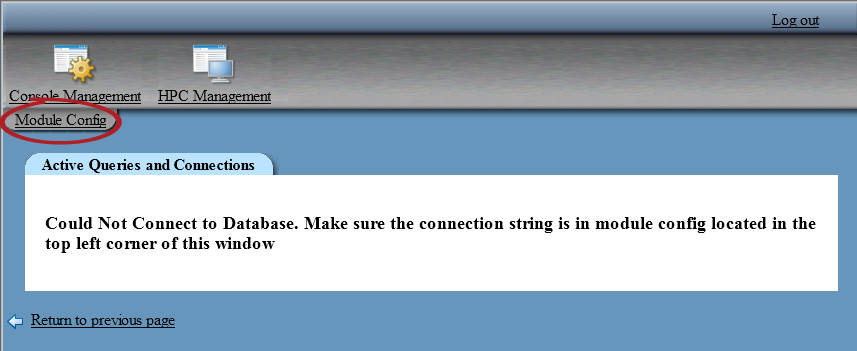
When you first access
the Active Queries and Connections module,
the console cannot connect to the Greenplum database because it is
not configured with the connection parameters. The following display
shows an example of the console before it is configured.
Unconfigured Active Queries and Connections
To configure the module:
-
Active Queries and Connections ConfigurationEnter the name of a database user account that has been granted the superuser role. For information about securing this user account, see Restrict the Database User Account.
Restrict the Database User Account
The database user account
that is used for the Greenplum Database connection must have superuser
privileges in order to monitor queries and terminate connections.
You can increase the security for the account by configuring Greenplum
Database to accept connections for the account from the machine that
hosts the console.
To restrict the database
user account: