Setting Up a Metadata-Bound Library
Overview of Setting Up a Metadata-Bound Library
-
If you want to support access from clients that use metadata in order to locate data, make sure that the physical library and tables are also registered in metadata (using the Data Library Manager plug-in within SAS Management Console). For example, to make the data available from within SAS Web Report Studio, you might register it beneath the
Shared Datafolder.
Tip
Binding a physical library
introduces additional constraints on access, so it is a good practice
to review existing access patterns beforehand. For help resolving any
unanticipated disruptions in end-user access, see Facilitate End-User Access.Who Uses the CREATE Statement?
Introductory Demonstration
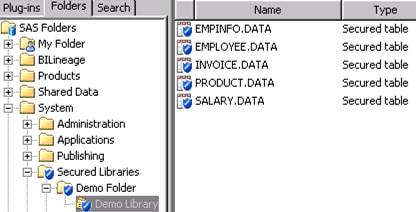
As a simple demonstration,
limit access to a library that contains tables copied from the SASHELP
library.
-
proc authlib library=secdemo; create securedfolder='/System/Secured Libraries/Demo Folder' securedlibrary='Demo Library' pw=secret; run;
Here are some details about the preceding code: -
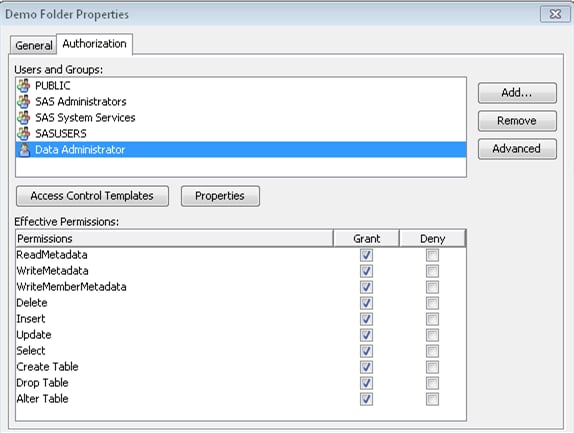
If you want to support access from clients that use metadata to locate data, register the library and tables in metadata (using the Data Library Manager plug-in within SAS Management Console).TipPermissions on a traditional library or table object can further limit access. For example, a user who reads data through the META LIBNAME engine (MLE) must have permissions on both the traditional table object (the ReadMetadata and Read permissions) and the secured table object (the ReadMetadata and Select permissions).
Set Up Mutually Exclusive Access
To
establish several distinct levels of access, set up a metadata folder
structure with appropriate permissions. Each secured library object
inherits permissions from its metadata folder. Each secured table
object inherits permissions from its parent secured library object.
The following example
demonstrates one way to set up mutually exclusive access for two user
groups (GroupA and GroupB) to four libraries (LibraryA1, LibraryA2,
LibraryB1, and LibraryB2). The example assumes that the following
prerequisites are met:
-
Constrain access at the
Secured Librariesfolder. One way to do this is to explicitly deny all permissions to the PUBLIC group and explicitly grant all permissions to the SAS Administrators group. These protections flow throughout the Secured Libraries branch, except where modified by additional direct access controls. -
Explicit Grants1
1For conciseness, this example uses individual explicit controls (instead of ACTs) and provides only Read access (the Select permission). These settings don’t allow members of GroupA and GroupB to update or delete data. -
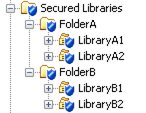
To bind the physical data to metadata, submit SAS code. Be sure to specify
FolderAas the metadata location for the first two libraries, andFolderBas the metadata location for the last two libraries.proc authlib; create library=liba1 securedfolder='FolderA' securedlibrary='LibraryA1' pw=secret; create library=liba2 securedfolder='FolderA' securedlibrary='LibraryA2' pw=secret; create library=libb1 securedfolder='FolderB' securedlibrary='LibraryB1' pw=secret2; create library=libb2 securedfolder='FolderB' securedlibrary='LibraryB2' pw=secret2; run;
Set Up Fine-Grained Access
Overview
Column-Level Access
In this example, partial
access to a customer data table is provided by creating a view and
managing access to it. The view keeps the name and telephone number
columns from the underlying table, but excludes the credit card number
column.
options metauser="sasadm@saspw" metapass="********" metaserver="machine.company.com"; libname cust 'path'; proc authlib library=cust; create securedlibrary='cust' securedfolder='CustomerData' pw=secret; quit; proc sql; create view cust.PUBLIC as select Name, Phone from PRIVATE(pw=secret); quit;
The preceding code creates
a new secured library object (CustomerData) that contains two objects:
a table object (called PRIVATE) and a view object (called PUBLIC).
Note: The password that is supplied
to bind the library is also supplied when the PUBLIC view is defined
against the PRIVATE table. In order to create a view of a metadata-bound
table, you must know the password of that physical table’s
parent library, and provide that password in the view definition.
You can enable end users to access the view without giving them access
to the underlying table. In effect, this provides selective access
to the columns and rows within the underlying table.
Note: If you modify the password
for the metadata-bound library, you must also update the view definition
with the new password.
Note: This example also demonstrates
how you can explicitly provide metadata server connection information
in an OPTIONS statement.
Identity-Driven, Row-Level Access
In this example, partial
access to an employee information table (HR.EMPINFO) is provided by
creating a view (HR.PERSONAL) that dynamically filters rows in the
underlying table. The filtering is based on each requesting user’s
authenticated user ID. The filtering relies on a security associations
table, which maps each user’s authenticated user ID to a corresponding
employee ID.
The following code creates
the identity-driven view of the employee information table. When requesting
users access the view, they retrieve only those rows that match the
user ID with which they authenticated to the metadata server.
proc sql;
create view hr.personal as
select a.*
from hr.empinfo(pw=secret) a,
hr.security(where=(loginid=_METADATA_AUTHENTICATED_USERID_)) b
where b.loginid ne '' and a.empid = b.empid;
quit;
If you want to provide
broader access to certain users (for example, to enable department
managers to see information about their employees), you can enhance
the SECURITY table to include a column that maps employees to departments,
create an additional view that exploits that mapping, and set metadata-layer
permissions so that only department managers can use the new view.