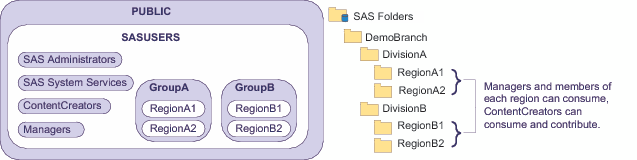
This example eliminates the project
folders and introduces the following requirements:
-
Regional employees see only content
for their region.
-
A central group of managers see
all content.
-
A central group of content creators
creates all content.
The following figure
depicts a partial group and folder structure.
The following table
lists the protections for the first four folders in the branch:
Subgroup Separation and Limited Contribution
|
|
|
|
|
|
 DemoBranch
|
 Protect
 LimitData
|
|
 DivisionA
|
 Hide
|
 GroupA: +RM
 ContentCreators: +RM
 Managers:+RM
|
 RegionA1
|
 Hide
|
 RegionA1: +RM, +R
 ContentCreators: +RM, +R, +WMM
 Managers:+RM, +R
|
 RegionA2
|
 Hide
|
 RegionA2: +RM, +R
 ContentCreators: +RM, +R, +WMM
 Managers:+RM, +R
|
Notice that you are
repeating many of the same explicit settings on each region, and that
this will be the case throughout the DemoBranch. For greater efficiency
and more centralized control, create a custom ACT (called RegionLevel)
that provides the supplemental grants for your content creators (RM,
R, WMM) and your managers (RM, R). Remember to protect the ACT itself.
The following table
lists the protections for the first four folders:
Use a Supplemental ACT
|
|
|
|
|
|
 DemoBranch
|
 Protect
 LimitData
|
|
 DivisionA
|
 Hide
|
 GroupA: +RM
 ContentCreators: +RM
 Managers:+RM
|
 RegionA1
|
 Hide
|
 RegionA1: +RM, +R
 RegionLevel
|
 RegionA2
|
 Hide
|
 RegionA2: +RM, +R
 RegionLevel
|
If you decide to offer
content at the division level and you want that content to be available
to only managers, you might make these changes:
-
Create a DivisionLevel ACT with
grants for Managers (RM, R) and ContentCreators (RM, R, WMM). Apply
that ACT to each division folder.
Note: This is the same pattern
that you use for the RegionLevel ACT, so you could instead simply
use that ACT. In this example, you choose to create a separate ACT
because you anticipate that the requirements for division-level access
and region-level access might diverge in the future.
-
Apply the Protect ACT on each region
folder (to take away the inherited grant of WriteMetadata permission
that content contributors inherit from their division-level grant
of WriteMemberMetadata permission).
Note: If you choose to not do this,
members of the content creators group can delete, rename, or change
permissions for the region folders.
The following table
lists the protections for the first four folders in the branch:
Accommodate Division-Level Content
|
|
|
|
|
|
 DemoBranch
|
 Protect
 LimitData
|
|
 DivisionA
|
 Hide
|
 GroupA: +RM
 DivisionLevel
|
 RegionA1
|
 Hide
 Protect
|
 RegionA1: +RM, +R
 RegionLevel
|
 RegionA2
|
 Hide
 Protect
|
 RegionA2: +RM, +R
 RegionLevel
|