Permissions
About Permissions
Key Points
Here are the key points
about permissions:
-
-
SAS Visual Analytics supports row-level security. SAS Visual Analytics does not support column-level security.Note: Do not set denials of the ReadMetadata permission on individual columns within a table. If a table is loaded by a user who lacks access to one or more columns, duplicate metadata entries are created for the unavailable columns.
-
In the administrator, you can set folder, library, table, and row-level permissions. For alternate interfaces, see Access Management in the SAS Intelligence Platform: Security Administration Guide.Note: In the administrator, you cannot view or set permissions on the objects that support metadata-bound libraries (secured library folders, secured libraries, and secured tables).
-
Access to each object is displayed as part of the object’s properties. Not all permissions are relevant for all objects.
-
Do not block ReadMetadata access for the SAS Trusted User (for example, sastrust@saspw). To preserve access, grant the ReadMetadata permission to the SAS System Services group.
-
For simplicity, set permissions on folders, not on individual objects. Most objects (including tables) inherit permissions from their parent folders. To learn how to customize the metadata folder structure, see Working with SAS Folders in the SAS Intelligence Platform: System Administration Guide.
-
For simplicity, assign permissions to groups, not to individual users. The broadest group is called PUBLIC. The SASUSERS group includes all registered users. To learn how to manage permissions systematically using access control templates, see Access to Metadata Folders in the SAS Intelligence Platform: Security Administration Guide.
Permission Definitions
The following table
documents permissions that have a special purpose in SAS Visual Analytics,
and introduces some of the standard permissions.
|
Permission
|
Affected Actions
|
|---|---|
|
Administer (A)
|
On a LASR library, load
and import tables.
On a SAS LASR Analytic
Server, stop the server or set a tables limit.
|
|
Read (R)
|
On a LASR table, read
data.
On a LASR library, load
and import tables.
On
an encrypted SASHDAT library, add, delete, or load data.
|
|
Write (W)
|
On a LASR table, unload
and reload the table; append and delete rows; and edit computed columns.
|
|
ReadMetadata (RM)
|
View an object. For
example, to see an exploration, report, table, or library, you need
the ReadMetadata permission for that object.
|
|
WriteMetadata (WM)
|
Edit, rename, set permissions
for, or delete an object; create certain associations among objects.
|
|
WriteMemberMetadata
(WMM)
|
On a folder, add or
remove objects.
|
For more information,
see Metadata Authorization Model in the SAS Intelligence Platform: Security Administration Guide.
Permissions by Task
LASR Tables and Servers
The following table documents
metadata-layer permissions for working with LASR tables and SAS LASR
Analytic Servers.
|
Task
|
Server
|
Library
|
Folder
|
Table
|
|---|---|---|---|---|
|
Read data
|
RM
|
RM
|
RM
|
RM, R
|
|
Append or delete rows
|
RM
|
RM
|
RM
|
RM, R, W
|
|
Edit computed columns
|
RM
|
RM
|
RM
|
RM, R, W
|
|
Load or import a table1
|
RM
|
RM, R, WM, A
|
RM, R, WMM, W
|
-
|
|
Load a stop list
|
RM, WM
|
RM, R, WM, A
|
RM, R, WMM, W
|
-
|
|
Reload a table
|
RM
|
RM
|
RM
|
RM, R, WM, W
|
|
Unload a table
|
RM
|
RM
|
RM
|
RM, R, W
|
|
Start a server
|
RM
|
-
|
-
|
-
|
|
Stop a server
|
RM, A
|
-
|
-
|
-
|
|
Set a server’s
tables limit
|
RM, WM, A
|
-
|
-
|
-
|
|
Assign a library to
a server
|
RM, WM
|
RM, WM
|
-
|
-
|
|
Register a table in
metadata
|
-
|
RM, WM
|
RM, WMM
|
-
|
|
Update a table’s
metadata
|
-
|
RM
|
RM
|
RM, WM
|
|
Delete a table from
metadata
|
-
|
RM, WM
|
RM, WMM
|
RM, WM
|
| 1An initial load (or import) creates a new LASR table object. Read and Write permissions on the folder support actions against the new table. | ||||
Explorations and Reports
The following table
documents metadata-layer permissions for working with reports and
explorations.
|
Task
|
Server
|
Table
|
Folder
|
Report
|
Exploration
|
|---|---|---|---|---|---|
|
Open a report or exploration
|
RM
|
RM, R
|
-
|
RM
|
RM
|
|
Export a report or exploration
|
RM
|
RM, R
|
-
|
RM
|
RM
|
|
Modify a report or exploration
|
RM
|
RM, R
|
-
|
RM, WM
|
RM, WM
|
|
Save a new report or
exploration
|
-
|
RM
|
RM, WMM
|
-
|
-
|
|
Delete a report or exploration
|
-
|
RM
|
RM, WMM
|
RM, WM
|
RM, WM
|
To create, update, or
delete a report, access to the SAS Content Server is also required.
See Administering the SAS Content Server in
the SAS Intelligence Platform: Middle-Tier Administration Guide. To view the data that populates
a report, ReadMetadata permission for the library where the data is
stored is also required. See the first row in Permissions for Working with LASR Tables and Servers.
Data Queries and LASR Star Schemas
The following table
documents metadata-layer permissions for working with data queries
and LASR star schemas.
|
Task
|
Server
|
Table2
|
Folder
|
Query or Schema
|
|---|---|---|---|---|
|
Save a new query or
schema1
|
RM
|
RM
|
RM, WMM
|
-
|
|
Run a query or schema1
|
RM
|
RM
|
-
|
RM
|
|
Edit and save a query
or schema
|
RM
|
RM
|
RM
|
RM, WM
|
|
Delete or rename a query
or schema
|
RM
|
-
|
RM, WMM
|
RM, WM
|
| 1These tasks create new LASR tables, so the permission requirements for loading a LASR table must also be met. See Permissions for Working with LASR Tables and Servers. | ||||
| 2This column refers to any source tables that are represented in metadata. To run a query or schema against a LASR table, Read permission for the LASR table is also required. | ||||
Read access to data
in a LASR star schema is not affected by permissions for input tables.
Instead, Read access to data in a LASR star schema is affected by
the Read and ReadMetadata permissions for the output table or view.
ReadMetadata permission for the associated server, library, and folder
is also required. See the first row in Permissions for Working with LASR Tables and Servers.
Note: You can set explicit access
controls (including permission conditions) on the output table or
view for a LASR star schema. Any explicit access controls persist
when you rerun the LASR star schema.
Grant or Deny a Permission
To set an explicit
grant or denial:
-
In the administrator’s Folders pane, right-click on an object, and select Authorization.TipTo display the Folders pane, select View
 Folders from the main menu.
Folders from the main menu.
-
In the Effective Permissions table, locate the identity to which you want to assign an explicit control. If the identity is not listed, click
 to open the Add Identities window.
Note: In the Add Identities window, only user administrators can successfully search by user ID. Regular users cannot see other users’ IDs.Note: An explicit grant of the ReadMetadata permission is automatically set for each identity that you add.
to open the Add Identities window.
Note: In the Add Identities window, only user administrators can successfully search by user ID. Regular users cannot see other users’ IDs.Note: An explicit grant of the ReadMetadata permission is automatically set for each identity that you add. -
Double-click on a cell. From the cell’s drop-down list, select either Deny or Grant.
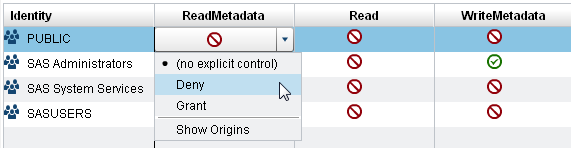 When the drop-down list collapses, notice that the cell contains an explicit control indicator
When the drop-down list collapses, notice that the cell contains an explicit control indicator .
Note: If the selected identity is an unrestricted user, all permissions are granted and you cannot make changes.
.
Note: If the selected identity is an unrestricted user, all permissions are granted and you cannot make changes. -
If you changed a group's access, review the impact on the other listed identities. Controls that you add for a group can affect access for all members of that group.
-
In the toolbar at the top of the tab, click
 .
.
Set a Row-Level Permission Condition
To limit Read access to rows in a LASR table:
-
In the administrator’s Folders pane, right-click on a LASR table, and select Authorization.TipTo display the Folders pane, select View
 Folders from the main menu.
Folders from the main menu.
-
In the Read column, double-click on the cell for the identity whose row-level access you want to constrain. (Or, if the identity is not listed, click
 at the right edge of the table.)
Note: An explicit grant of the ReadMetadata permission is automatically set for each identity that you add.
at the right edge of the table.)
Note: An explicit grant of the ReadMetadata permission is automatically set for each identity that you add. -
From the cell’s drop-down list, select Conditional grant.
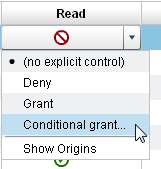 Note: If Conditional grant is not in the drop-down list, the table does not support row-level security. Only LASR tables support row-level security.Note: If Conditional grant is already selected, select Conditional grant again to view or edit the existing condition.
Note: If Conditional grant is not in the drop-down list, the table does not support row-level security. Only LASR tables support row-level security.Note: If Conditional grant is already selected, select Conditional grant again to view or edit the existing condition. -
In the New Permission Condition window, create a condition that specifies which rows the identity can see. See Syntax (Enhanced Editor).Note: Conditions from releases prior to 6.2 or from batch tools use a basic editor. In the basic editor, syntax is not validated. See Syntax (Basic Editor, Batch).
-
Click OK. Notice that the cell contains the conditional grant icon
 with an explicit control indicator
with an explicit control indicator  .
.
-
If you set a permission for a group, review the impact on the other listed identities. Constraints that you add for a group can affect access for all members of that group.
-
In the toolbar at the top of the tab, click
 .
.
Tip
When you test conditions in
another application (such as the explorer), refresh the data source
in that application so that your changes are reflected. See Caching.A permission condition
constrains Read access to rows within a LASR table. For more information,
see Row-Level Security.
View Authorization Information
Here are some details about the Authorization page:
-
Each object’s Authorization page describes access to that object. The displayed effective permissions are a calculation of the net effect of all applicable metadata-layer permission settings. To identify the source of an effective permission, double-click on its cell, and select Show Origins from the drop-down list. See Permission Origins.
-
Icons indicate grants
 , conditional (row-level) grants
, conditional (row-level) grants  , and denials
, and denials  .
.
-
The explicit indicator icon
 indicates an access control that is explicitly set
on the current object and explicitly assigned to the selected identity.
indicates an access control that is explicitly set
on the current object and explicitly assigned to the selected identity.
-
The ACT indicator icon
 indicates an access control that comes from an applied
ACT whose pattern assigns the grant or denial to the selected identity.
indicates an access control that comes from an applied
ACT whose pattern assigns the grant or denial to the selected identity.
-
In combination, icons provide information as follows:IconMeaning

 Grant from an explicit control
Grant from an explicit control
 Grant from a directly applied ACT
Grant from a directly applied ACT Grant from an indirect source (such as a parent group or parent object)
Grant from an indirect source (such as a parent group or parent object)
 Conditional grant from an explicit control
Conditional grant from an explicit control Conditional grant from an indirect source (a parent group)
Conditional grant from an indirect source (a parent group)
 Denial from an explicit control
Denial from an explicit control
 Denial from a directly applied ACT
Denial from a directly applied ACT Denial from an indirect source (such as a parent group or parent object)
Denial from an indirect source (such as a parent group or parent object) -
To compare permissions for two tables, open them both, and then select View
 Tab Layout
Tab Layout Stacked from the main menu.
Stacked from the main menu.
Copyright © SAS Institute Inc. All Rights Reserved.
Last updated: December 18, 2018