Firewall Configurations
Setting Up a Firewall Configuration That Uses Restricted Ports
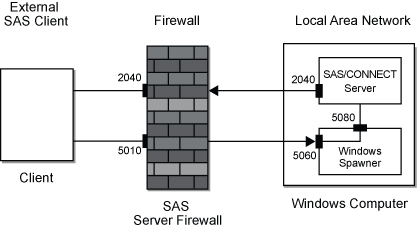
The example configuration
includes an external SAS client, a firewall, and a
SAS/CONNECT server session and a spawner program
that run on the local area network. Each external client connects
to the server using a range of restricted ports.
-
Note: Restricted ports are implemented using the TCPPORTFIRST= and TCPPORTLAST= system options that are specified in the SAS start-up file. (See step 4).
-
The administrator of the
SAS/CONNECT SAS/CONNECT SAS is started and the restricted port is 2040. In this example, all communications between external SAS clients and theSAS/CONNECT A range of ports could be specified by increasing the values assigned to the TCPPORTFIRST= and TCPPORTLAST= system options. For details about the system options under Windows, see TCPPORTFIRST= and TCPPORTLAST=; for UNIX, see TCPPORTFIRST= and TCPPORTLAST= . -
The administrator of the
SAS/CONNECT The restricted port that is used by the SAS client and theSAS/CONNECT mysas.cmdscript via the TCPPORTFIRST= and TCPPORTLAST= system options.For details about spawner options, see SAS/CONNECT Spawners.
Setting Up a Firewall Configuration That Uses a Single Port
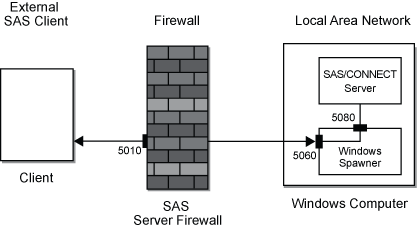
The example configuration
includes an external SAS client, a firewall, and a
SAS/CONNECT server session and a spawner program
that run on the local area network. Each external client connects
to the server using a single port, which is enabled by socket inheritance.
-
The administrator of the
SAS/CONNECT Note: Windows uses thespawnercommand; UNIX uses thesastcpdcommand. The -INHERITANCE option can be omitted from the command because the option is enabled, by default. Socket inheritance implements the use of a single port.For details about spawner options, see SAS/CONNECT Spawners.