Choices in Workspace Server Pooling
About Workspace Server Pooling
The primary
purpose of pooling is to enhance performance by avoiding the time
penalty that is associated with launching all workspace servers on
demand. In pooling, a set of workspace servers are made available
to process certain types of query requests. In general, pooling is
used when a relational information map is queried, processed, opened,
or used indirectly (through a report).
Benefits and Risks of Server-Side Pooling
Server-side pooling offers the following
benefits:
-
With server side-pooling, the spawner can request user-specific metadata-layer access evaluations, such as whether a user has permission to use a particular server. This isn't possible in client-side pooling because use of the pool administrator prevents the spawner from knowing who the requesting user is.
-
A side effect of pooling is that the launched workspace servers run under a designated service account. This side-effect is beneficial in avoiding credential gaps that can occur when a desktop application requests a workspace server from a middle-tier service. This benefit is not provided by client-side pooling, because client-side pooling is supported only for Web applications.
Server-side pooling
introduces the following risks:
-
Someone might write a rogue application that bypasses metadata layer access controls. This risk originates from the following difference in server control:
-
In server-side pooling, there is no pool administrator or alternate form of application-based gatekeeping. Anyone who can use the server legitimately (from a SAS application) can also exploit that server by writing a rogue application that uses the server to fetch SAS tables. The security issue is that retrieval from such an application bypasses metadata-layer controls that apply when the same data is accessed in a legitimate manner. For example, a request in SAS Web Report Studio might be filtered by a metadata-layer permission condition that enables the user to see only certain rows in a data set.
-
Someone might exploit the server-side pooled workspace server from within SAS Information Map Studio. In general, only information map creators who have host access to the target data use this application. If someone else has SAS Information Map Studio, that person could bypass metadata-layer controls when querying a relational information map from within that application.
The following table summarizes the trade-offs. For completeness,
the table includes a column for a standard workspace server that uses
SAS token authentication and a column for a standard workspace server
that uses either form of host authentication (credential-based or
Integrated Windows authentication).
Summary: Comparison of Workspace Server Configurations
|
Accommodates batch generation
of scheduled reports.1
|
||||
|
Fully compatible with
Integrated Windows authentication.2
|
||||
|
The user (or group)
host identity is passed to SQL Server.3
|
||||
| 1Credentials for the workspace server are available to the batch generation process. | ||||
| 2Accommodates requests through SAS Intelligent Query Services for a workspace server (for example, opening an information map after logging on to SAS Enterprise Guide using Integrated Windows authentication). | ||||
| 3If the workspace server's host authentication is by IWA and any additional configuration requirements are met. | ||||
Which Requests Are Eligible to Use Pooling?
Only requests that are handled by a particular query
services software component are eligible to use pooling. That software
component is primarily used to query, process, open, or otherwise
interact with a relational information map.
Note: In SAS Enterprise Guide and
the SAS Add-In for Microsoft Office, not all such requests are eligible.
If the libraries that an information map references can be assigned
within an existing SAS session, a request to open that information
map is not eligible to use pooling. To ensure that such requests are
eligible, limit physical (host operating system) access to the directories
that are referenced by that information map's libraries. Deny access
to users and grant access to the host identity under which a pooled
server runs.
Note: Similar requests that don't
involve a relational information map aren't eligible, because those
requests aren't handled by the query services component. For example,
requests to open a report that directly contains a stored process
or open a report that contains OLAP data are not eligible.
Which Eligible Requests Actually Use Pooling?
Use of pooling for eligible requests
is constrained as follows:
can be used for eligible
requests in only specially configured Web applications. For example,
if SAS Web Report Studio's configuration includes a pool administrator,
that application uses client-side pooling to process information maps.
can be used for eligible
requests in any application. For example, server-side pooling can
be used to process information maps from SAS Web Report Studio, SAS
Information Map Studio, SAS Enterprise Guide, and the SAS Add-In for
Microsoft Office. However, eligible requests don't use server-side
pooling in the following circumstances:
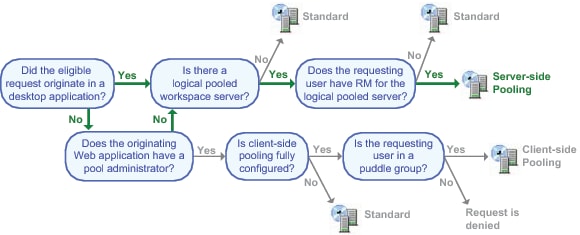
The following figure
summarizes the decision sequence that determines what type of server
processes an eligible request. Most of the determinative factors can
be controlled by an administrator.
Modifying the Initial Pooling Configuration
If you are concerned about the risk that server-side
pooling introduces, and that concern outweighs the advantages of server-side
pooling, consider these options:
-
To enable information map creators to run queries under their own host identities (instead of under the launch credential of the server-side pooled workspace server), hide that server definition from those users. Someone who can't see the logical pooled workspace server uses the standard workspace server instead.Note: This is appropriate only if you have an information map creator who shouldn't be able to access all data that is available to the pooled workspace server. This doesn't eliminate the risk of unauthorized use of SAS Information Map Studio by someone who legitimately uses the server-side pooled workspace server from other applications.
See Also
Understanding Server Pooling in SAS Intelligence Platform: Application Server Administration Guide