Understanding Firewalls and Application Dispatcher
This document discusses the use of firewalls with the SAS/IntrNet Application Dispatcher for Release 8.1 and later. For earlier releases, please refer to the documentation for that release. A brief description of network firewalls and the Application Dispatcher is followed by a discussion of various firewall configurations and the corresponding advantages and disadvantages.
Web servers and other network applications often use firewalls to limit access to sensitive data. A firewall is a controlled gateway between one network and another. Firewalls are commonly used to provide a secure connection between an internal network and the Internet, but they may also be used to control access between multiple internal networks with different classes of users. The firewall typically acts as a proxy to make connections between the two networks. A connection might be allowed or denied based on service (socket address), network address, authentication information (username and password), or other criteria.
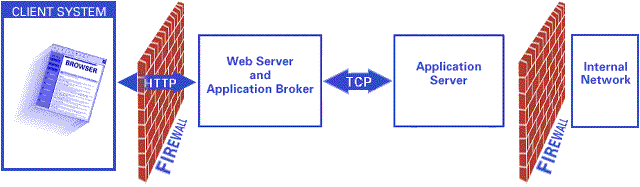
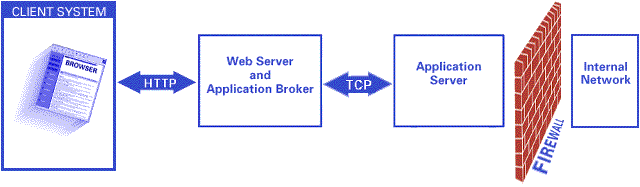
The SAS/IntrNet Application Dispatcher is a three-tier network application as shown in the figure below.
The SAS/IntrNet application client is typically a Web browser. The Web browser uses the network to make an HTTP connection to a Web server. The Web server runs the Application Broker CGI program. The Broker contacts the SAS Application Server at a predefined "well-known" TCP socket address. The user request is passed to the Application Server on this connection. The response from the Application Server is returned on the same connection.
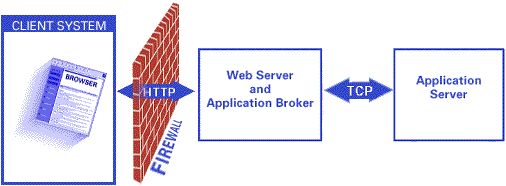
Case 1: Web Server inside the Firewall
A firewall can be placed between the Web server and the clients (for example, the Internet). The firewall allows only HTTP connections from clients to the Web server. No other network ports (such as the Application Server port) are directly reachable by clients.
Advantages:
- The firewall is easy to configure and understand.
- The Application Server port is not exposed to malicious clients.
- The Application Dispatcher has no special requirements: both the Broker and the Application Server are inside the firewall.
Disadvantages:
The Web server has access to the entire internal network. The Web server must be carefully configured to avoid exposing private data.
- Security flaws in the Web server potentially compromise the firewall. The Web server is generally more complex than a firewall and harder to verify.
Case 2: Firewall between the Web Server and Application Server
A firewall can be placed between the Web server and the internal network that includes the Application Server. This is a common situation because the Web server is usually considered an untrusted component, while the Application Server generally has direct access to internal data sets.
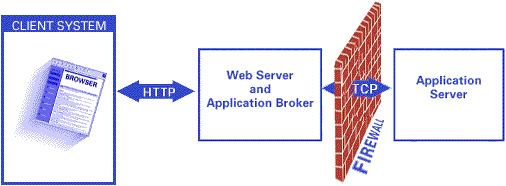
Note that the Application Server port is exposed to clients outside the firewall. A malicious client can bypass the broker and connect directly to the Application Server. Application Server programs should be written with this in mind. Programs that access sensitive data should require passwords or perform some other form of access control.
If the Load Manager is used in this case, it usually runs on the Application Server side of the firewall. The firewall must also allow connections from the Broker to the Load Manager port.
Advantages:
- The Web server is outside the firewall.
- The Application Server has full access to internal data sets and servers.
Disadvantages:
- The Application Server is exposed to clients. Applications must implement some level of security.
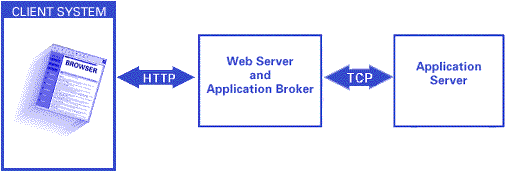
Case 3: Web Server and Application Server outside the Firewall
The Application Server can be placed with the Web server outside the firewall. This approach simplifies the firewall configuration but limits the Application Server. This approach works well if data that is used by the application can be built or copied outside the firewall. Data inside the firewall can be accessed through a SAS/SHARE server if the firewall is configured to allow the Application Server to connect to the SAS/SHARE port. This configuration might expose the SAS/SHARE server to external access.
Advantages:
- The Web server is outside the firewall.
- The firewall is simple to configure.
- This configuration is simple to understand: external applications are external to the firewall.
Disadvantages:
Data must be moved or copied outside the firewall (or SAS/SHARE must be used to access data through the firewall).
- The SAS/SHARE server (if any) is exposed to clients. The server should have limited access to internal data and typically is password protected.
Case 4: Multiple Firewalls
Security can be improved by combining the above configurations — for example, cases one and three. A firewall between the Web server and the Internet that allows only HTTP connections can provide some degree of protection against direct access to the Application Server. A second firewall that separates the Web server and Application Server from the internal network enables tighter control of data access by Web applications.