Authorization Model for Metadata-Bound Tables
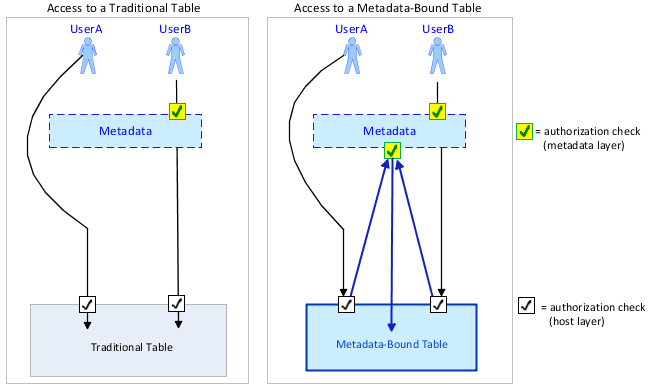
The following figure
depicts the authorization model for a traditional table and a metadata-bound
table. In both cases, UserA references the target data directly (for
example, through a LIBNAME statement) and UserB requests the target
data through a client that uses metadata to locate data (for example,
SAS Web Report Studio).
For the metadata-bound
table, the upwards-facing arrows are caused by the physical data’s
security binding. For each metadata-bound table, information within
the table header identifies a corresponding metadata object (a secured
table object). Metadata-layer permissions on each secured table object
affect access from SAS to the corresponding physical table.
For the metadata-bound
table, UserB is subject to two metadata-layer authorization checks
against two different metadata objects.
Tip
In the SAS metadata, traditional
table objects and secured table objects are distinct and independent
types of objects. See Object Creation, Location, and Inheritance.