Access Control Inheritance
About the Explore Inheritance Diagram
The Explore Inheritance
diagram enables you to identify all of the access control parents
for object. You can also use this diagram to easily see, for a particular
user and permission, where in an object’s inheritance path
access is gained or lost. For information about permissions, see SAS Intelligence Platform: Security Administration Guide.
To access the Explore
Inheritance diagram, open the object of interest, select the Authorization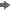 Basic tab, and click
Basic tab, and click  (in the toolbar at the right of the table).
(in the toolbar at the right of the table).
 (in the toolbar at the right of the table).
(in the toolbar at the right of the table).
Tip
The Explore Inheritance diagram
shows access control inheritance relationships (such as "a cube
inherits effective permissions from its folder"), not lineage
relationships (such as "a cube depends on its parent schema").
For example, an information map might use a cube and therefore depend
on that cube, but there is no access control relationship between
the information map and the cube. The information map and the cube
both inherit access controls from their parent folders.
Examples of Explore Inheritance Diagrams
The following figure
shows a simple example of an Explore Inheritance diagram.

In the preceding example,
the diagram was launched from the Shared Data folder
object, so that object is the left-most object in the display. The
immediate parent of Shared Data is SAS
Folders. SAS Folders inherits
from the repository itself, which is represented by the Default
ACT because that access control template (ACT) pattern
controls access at the repository-level. If you use the controls at
the top of the diagram to show effective permissions for a particular
user and permission (for example, the SAS Demo User and the ReadMetadata
permission), the display might look like the following figure:

In the preceding example,
the selected user has the selected type of access through the entire
inheritance path. If you use the controls at the top of the diagram
to select a different permission (for example, the WriteMetadata permission),
the display might look like the following figure.
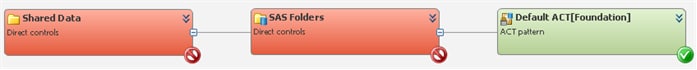
In the preceding example,
the selected user has the selected type of access at the repository-level,
but loses that access at the SAS Folders node.
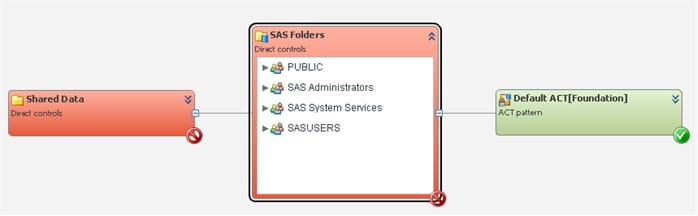
One way to investigate why access is lost at that node is to examine
the details within that node. For example, you might find that the
PUBLIC group has an explicit denial of WriteMetadata, and no other
group that the selected user belongs to has a direct grant. In the
following figure, the SAS Folders node shows
its details.
Note: In the unusual circumstance
in which an object has more than one immediate parent, the diagram
has multiple branches. When an object has more than one inheritance
path, a grant from either path is sufficient to provide access.
Tips for Exploring Inheritance
Here are some tips for
using the Explore Inheritance diagram:
-
The diagram is read-only. You cannot open new object tabs from within the diagram or make changes from within the diagram.
-
Most objects have only one immediate parent, so the display is usually a simple horizontal chain of objects.
-
The current object (the object from which you launched the diagram) is the left-most node.
-
The orientation, from left to right, moves from child to parent (showing "inherits from" relationships).
-
You can use the buttons at the top of the diagram to quickly manipulate the entire display (for example, to expand the entire diagram or show details for all nodes).
-
Unsaved changes are not reflected in the diagram.
-
Each node contains details as follows:
-
For a right-most node (a node that represents a repository), the permission pattern of the repository’s ACT is displayed.
-
For other nodes:
-
If there are direct controls, those controls are displayed.
-
If there are no direct controls, the node does not have details.
-
-
-
When effective permissions are displayed, a status icon in the lower right corner of each node indicates whether the selected identity is granted or denied the selected permission. You can click on a status icon to view origins information for that effective setting.
-
Not all permissions are applicable to all types of objects, so the permission drop-down list does not always list all permissions. Only the permissions that are relevant for the current object (the left-most node) are listed. For example, only ReadMetadata and WriteMetadata are supported for reports, so when you launch the diagram from a report only those two permissions are offered in the permissions drop-down list.
-
If you lack ReadMetadata access to any of the parent objects, the left-most node to which you lack ReadMetadata access is indicated as Unknown, and no further nodes are displayed.
-
When you examine effective access for the WriteMetadata (WM) or WriteMemberMetadata (WMM) permission, remember that inheritance of these permissions is specialized. WMM on a parent folder becomes WM on the child items within that folder; WM itself is not inherited from folders.Note: Folders that represent repositories (for example, the SAS Folders node) are software components (not true folders), so they do not support WMM. When you examine effective WMM permissions, folders that represent repositories do not show an effective permission.
Copyright © SAS Institute Inc. All Rights Reserved.
Last updated: February 22, 2018