Controlling Access to SAS Environment Manager
About Native Roles and Users
SAS Environment Manager
controls access and permissions within the application with its own
registry of users and its own system of roles and permissions. In
order to distinguish between the SAS Environment Manager access features
and those in SAS metadata, this document and the SAS Environment Manager
online Help refers to features internal to SAS Environment Manager
as native features (such as native users or native roles). However,
the SAS Environment Manager interface does not use the native terminology.
Although native user
definitions are internal to SAS Environment Manager, they are mapped
to user definitions created in SAS metadata. Native users are created
by first creating the user definition in metadata and then synchronizing
the user information with SAS Environment Manager. You cannot create
native user definitions in SAS Environment Manager directly.
Native roles enable
you to grant capabilities and permissions for actions in SAS Environment
Manager to selected users. For example, an administrator role could
be granted full permissions for all resource types and the ability
to acknowledge and fix alerts, while a guest role could be denied
the ability to fix or acknowledge alerts and have only Read permission
for resources. Assigning a native role to a native user determines
the actions that the user can perform in SAS Environment Manager.
Each
native role also has its own unique Dashboard page.
Each user has access to their own personal Dashboard page
and the Dashboard pages of all native roles
of which they are a member.
SAS Environment Manager and SAS Metadata Users
Users in SAS Environment
Manager are mapped to users created in SAS metadata. During installation,
three user groups are created in SAS metadata to contain SAS Environment
Manager users. Users and subgroups that are members of these groups
are mapped to user definitions in SAS Environment Manager with corresponding
roles. The user groups and their corresponding roles are as follows:
|
Group name in SAS metadata
|
Role in SAS Environment
Manager
|
|---|---|
|
SAS_EV_Super_User
|
Super User role
|
|
SAS_EV_Guest
|
Guest role
|
|
SAS_EV_AppServer_Tier
|
SAS App Tier role
|
For example, users that
are members of the group SAS_EV_Guest in metadata are created as users
in SAS Environment Manager and are assigned to the Guest role when
the users are synchronized.
When you install SAS
Environment Manager, all existing SAS Environment Manager user definitions
are automatically added to the SAS_EV_Guest group in metadata. After
the existing users have been added to the SAS_EV_Guest group, use
SAS Management Console to modify the user definitions or assign users
to other SAS_EV groups in metadata.
After you have defined
new users in SAS metadata, sign on to SAS Environment Manager, and
select Manage Synchronize
Users. User definitions are created for
all users that are defined in the three SAS_EV groups in metadata.
Any SAS Environment Manager users that are not associated with user
definitions in metadata are deleted.
Synchronize
Users. User definitions are created for
all users that are defined in the three SAS_EV groups in metadata.
Any SAS Environment Manager users that are not associated with user
definitions in metadata are deleted.
If you sign on to SAS
Environment Manager using a user ID that is defined in metadata, is
a member of one of the SAS_EV groups, but is not defined in SAS Environment
Manager, then a user definition is automatically created in SAS Environment
Manager and assigned to the correct group.
The mapping between
user information in metadata and in a SAS Environment Manager user
definition is as follows:
|
Metadata field
|
SAS Environment Manager
field
|
|---|---|
|
Display Name
|
First Name and Last
Name
|
|
Name
|
First Name if the Display
Name is not specified
|
|
Account
|
Username
|
|
Email
|
Email
|
|
Phone
|
Phone
|
To create a new SAS
Environment Manager user, select Administration Users in SAS Environment Manager
to define the user and assign it to the appropriate SAS_EV user group,
and then select Manage
Users in SAS Environment Manager
to define the user and assign it to the appropriate SAS_EV user group,
and then select Manage Synchronize
Users to create the native user and assign
the user to the proper role.
Synchronize
Users to create the native user and assign
the user to the proper role.
The users in the SAS
App Tier role are automatically granted access to the resources in
these resource groups:
-
SAS App Tier group
-
SAS App Tier Server group
-
SAS App Tier Services group
An internal account,
sasevs (sasevs@saspw), is also created during installation. This account
is assigned to the SAS_EV_Guest group. The account is used for communications
between the SAS Environment Manager agent and server and enables plugins
to access the SAS Metadata Server. The internal account sasadm@saspw
is the default account for signing on to SAS Environment Manager.
CAUTION:
All accounts in the
SAS Environment Manager Super User group have access to the gconsole
plugin, which allows groovy code to be submitted. A side effect of
this capability is that groovy code can be executed as the server
process owner, which is typically the SAS installer account. If your
security policy does not permit this account to have this capability,
you can move or delete the gconsole plugin. Move or delete the directory
<levelroot>/Web/SASEnvironmentManager/server-5.8.0-EE/hq-engine/hq-server/webapps/ROOT/hqu/gconsole.
The SAS Logon
Manager is used to control the process of logging on to SAS Environment
Manager. The application uses the same authentication process and
authentication provider as the other SAS web applications.
Updating Passwords for SAS Environment Manager Metadata Identities
To update the password
for the sasevs@saspw account, follow these steps:
-
Stop all SAS Environment Manager agents on the system.
-
On the middle-tier machine, use the SAS Deployment Manager to change the password for the sasevs account.
-
Use the SAS Deployment Manager to update the sasevs password on the machines in the other tiers in the system.
-
Restart the SAS Environment Manager agents.
Creating a Native Role
To create a native role, follow
these steps:
-
On the Manage page, select New Role.
-
On the New Role page, specify a name for the role and select the native permissions and capabilities for each resource type. If you grant the Read Only permission for a resource type, you can also select the native capabilities for the resource type. For all other permissions, the capabilities are automatically selected or disabled and cannot be changed.
-
Use these guidelines to determine the native permissions to set:Adding a resource to the inventory and creating alert definitionsSelect Full or Read / Write permissions. Users can also respond to alerts and control resources.Monitoring resources, responding to alerts, controlling resourcesSelect the Read Only permission and grant the capability to acknowledge and fix alerts and to control resources. Users can respond to alerts and control resources but cannot create or modify alerts or resources.Monitoring resourcesSelect the Read Only permission, but do not grant capabilities for alerts resource control. Users can view and monitor only resources.
-
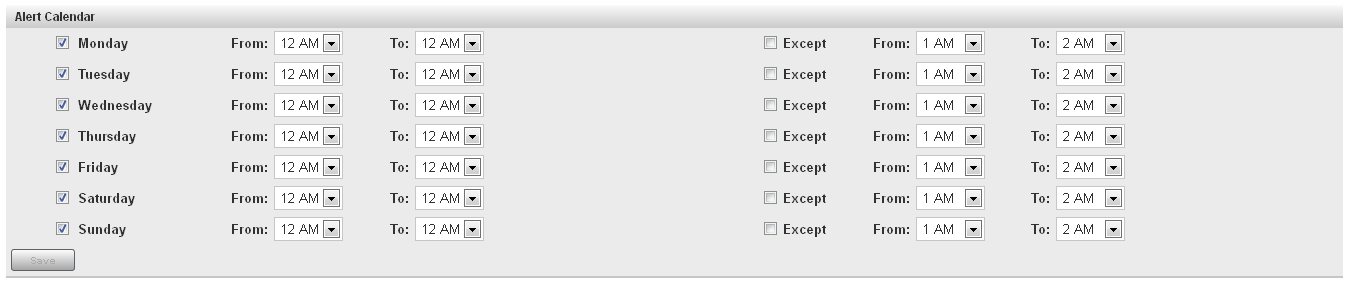
When you click OK, the role and associated Dashboard page are created, and the Role Properties page is displayed. Use this page to select native users and resource groups that should be associated with the role and to create an alert calendar.
-
To create an alert calendar, select the days and times during which the roles’ users will be notified of alerts. Make sure that at least one role is available during every time period.
Copyright © SAS Institute Inc. All Rights Reserved.
Last updated: February 22, 2018