Permission Origins
Introduction to Permission Origins
The permission origins
feature identifies the source of each effective permission. Permission
origins answers the question: Why is this identity granted (or denied)
this permission?
In the origins answer,
only the controlling (winning, highest precedence) access control
is shown. If there are multiple tied winning controls, they are all
shown. Other, lower precedence controls are not shown in the origins
answer.
Simple Permission Origins
The following table
provides simple examples of permission origins answers. In each example,
we are interested in why UserA has an effective grant on FolderA.
In each example, UserA is a direct member of both GroupA and GroupB.
Each row in the table is for a different (independent) permissions
scenario. In the table, the first column depicts the contents of the Origins window.
The second column interprets the information.
|
Origins Information
|
Source of UserA's Effective
Grant on FolderA
|
|---|---|
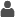 UserA [Explicit] UserA [Explicit]
|
On FolderA, an explicit
grant for UserA
|
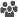 GroupA [Explicit] GroupA [Explicit]
|
On FolderA, an explicit
grant for GroupA
|
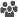 GroupA [Explicit] GroupA [Explicit]
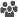 GroupB [Explicit] GroupB [Explicit]
|
On FolderA, explicit
grants for GroupA and GroupB
Note: Two settings are shown because
they are tied and they both win (UserA is a direct member of GroupA
and GroupB).
|
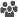 GroupA [ACT: GroupARead] GroupA [ACT: GroupARead]
|
On FolderA, an ACT pattern
grant for GroupA (from a directly applied ACT)
|
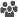 SASUSERS [ACT: GenRead] SASUSERS [ACT: GenRead]
|
On FolderA, an ACT pattern
grant for SASUSERS (from a directly applied ACT)
|
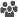 GroupA [ACT: GroupARead] GroupA [ACT: GroupARead]
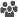 GroupB [ACT: GroupBRead] GroupB [ACT: GroupBRead]
|
On FolderA, ACT pattern
grants for GroupA and GroupB (from two different directly applied
ACTs).
Note: Two settings are shown because
they are tied and they both win (UserA is a direct member of GroupA
and GroupB).
|
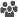 GroupA [ACT: GroupABRead] GroupA [ACT: GroupABRead]
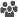 GroupB [ACT: GroupABRead] GroupB [ACT: GroupABRead]
|
On FolderA, ACT pattern
grants for GroupA and GroupB (from the same directly applied ACT).
Note: Two settings are shown because
they are tied and they both win (UserA is a direct member of GroupA
and GroupB).
|
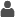 UserA is unrestricted. UserA is unrestricted.
|
UserA’s status
as an unrestricted user (someone who is unrestricted is always granted
all permissions)
|
|
This setting mirrors the WriteMetadata setting.
|
The WriteMetadata setting
on FolderA. To investigate further, examine the origins for that setting.
|
Inherited Permission Origins
In many cases, the controlling
setting is not on the current object. Instead, the controlling setting
is defined on a parent object and inherited by the current object.
The following table
provides examples in which the controlling setting comes from a parent
object. Because the source of the effective permission is a parent
object, the answer must identify which parent object has the controlling
setting. For this reason, the origins answers in the following examples
identify both a particular parent object (the object that has the
controlling setting) and the controlling setting itself.
In each example, we
are interested in why UserA has an effective grant on FolderA. In
each example, UserA is a direct member of both GroupA and GroupB.
Each row in the table is for a different (independent) permissions
scenario. In the table, the first column depicts the contents of the Origins window.
The second column interprets the information.
|
Origins Information
|
Source of UserA's Effective
Grant on FolderA
|
|---|---|
 ParentFolderA ParentFolderA
 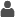 UserA [Explicit] UserA [Explicit]
|
On ParentFolderA, an
explicit grant for UserA
|
 ParentFolderA ParentFolderA
 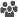 GroupA [Explicit] GroupA [Explicit]
|
On ParentFolderA, an
explicit grant for GroupA
|
 ParentFolderA ParentFolderA
 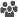 GroupA [Explicit] GroupA [Explicit]
 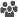 GroupB [Explicit] GroupB [Explicit]
|
On ParentFolderA, explicit
grants for GroupA and GroupB
|
 ParentFolderA ParentFolderA
 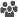 GroupA [ACT: GroupARead] GroupA [ACT: GroupARead]
|
On ParentFolderA, an
ACT pattern grant for GroupA (from a directly applied ACT)
|
 GreatGrandParentFolderA GreatGrandParentFolderA
 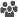 SASUSERS [ACT: GenRead] SASUSERS [ACT: GenRead]
|
On GreatGrandParentFolderA,
an ACT pattern grant for SASUSERS (from a directly applied ACT)
|
 ParentFolderA ParentFolderA
 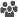 GroupA [ACT: GroupARead] GroupA [ACT: GroupARead]
 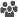 GroupB [ACT: GroupBRead] GroupB [ACT: GroupBRead]
|
On ParentFolderA, ACT
pattern grants for GroupA and GroupB (from two different directly
applied ACTs)
|
 GrandParentFolderA GrandParentFolderA
 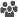 GroupA [ACT: GroupABRead] GroupA [ACT: GroupABRead]
 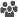 GroupB [ACT: GroupABRead] GroupB [ACT: GroupABRead]
|
On GrandParentFolderA,
ACT pattern grants for GroupA and GroupB (from the same directly
applied ACT).
|
 SAS Folders SAS Folders
 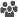 SASUSERS [Explicit] SASUSERS [Explicit]
Default ACT [CustomRepositoryA]
 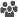 SASUSERS [Pattern] SASUSERS [Pattern]
|
On the SAS
Folders node, an explicit grant for SASUSERS.
Also, in CustomRepositoryA’s
default ACT, a pattern grant for UserA.
Note: In this example, FolderA
is within a custom repository, so it inherits from both the SAS
Folders node and the custom repository’s default
ACT pattern. Two settings are shown because they are tied and they
both win.
|
Copyright © SAS Institute Inc. All rights reserved.