Authentication to the Metadata Server
How SAS Identity Is Determined
-
In the SAS identity phase, the system resolves the authenticated user ID to a particular SAS identity. In this phase, SAS examines its copies of user IDs in an attempt to find one that matches the authenticated user ID. One of the following outcomes occurs:
-
A matching user ID is found, so a connection is established under the owning identity. The owning identity is the user or group whose definition includes a login with the matching user ID.Note: The metadata server's integrity constraints ensure that there won't be more than one owning identity. See Uniqueness Requirements.
-
No matching user ID is found, so a connection is established under the generic PUBLIC identity. In the metadata layer, the user is a PUBLIC-only user.Note: The matching process expects the SAS copy of the user ID to be qualified (if it is a Windows user ID).Note: Not all applications allow a PUBLIC-only user to log on. See PUBLIC Access and Anonymous Access.
-
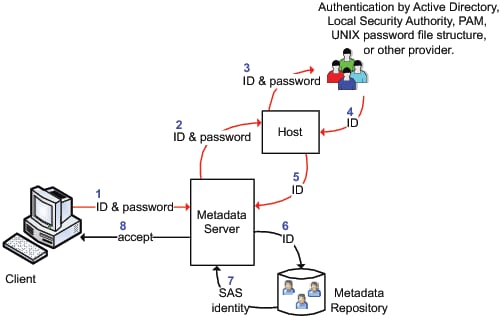
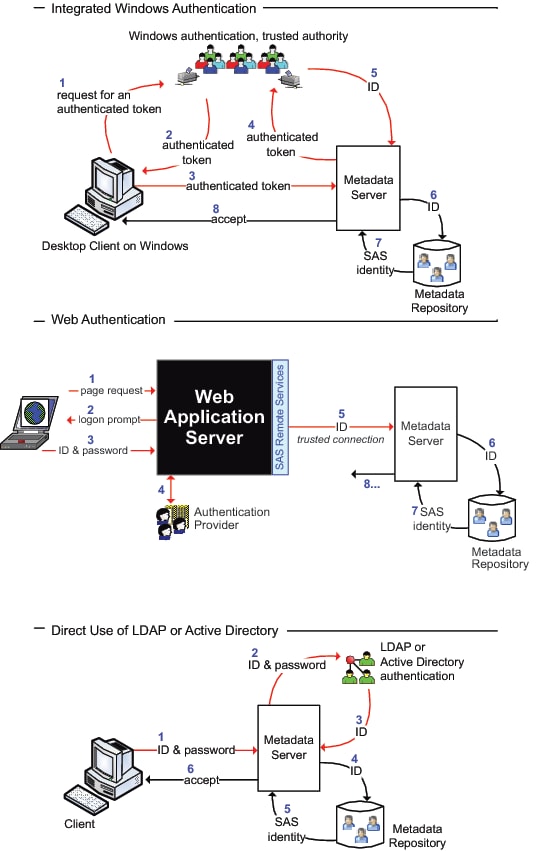
Authentication Process and Methods
The following figures
introduce the metadata server's authentication process and methods.
In the following figures, notice these points:
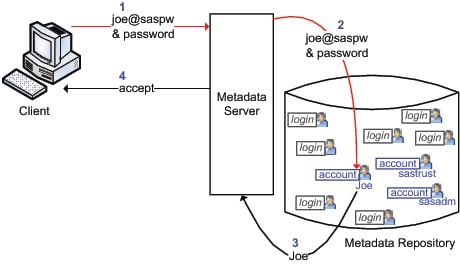
The following figure
depicts a special case where a metadata administrator named Joe uses
an internal account.