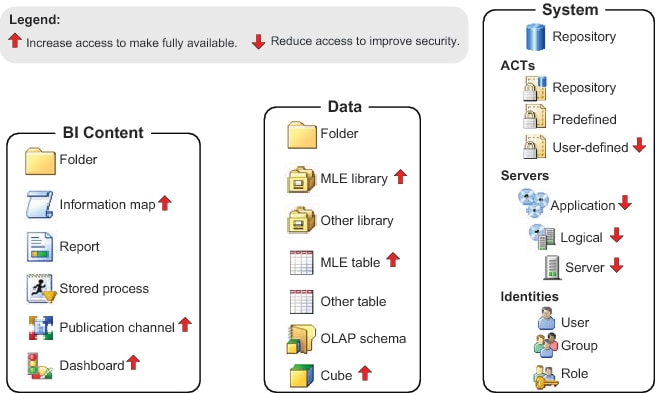
Permissions by Object Type
Introduction
The following figure depicts common objects and uses
arrows to indicate objects whose permission settings are most likely
to need an adjustment. Here are some details about the figure:
The following tables
provide object-specific instructions and tips. The purpose of the
tables is to highlight special requirements for common items.
Tip
For any change-managed areas
or resources, change-managed users should have CheckInMetadata (CM)
permission (instead of WM or WMM). See Setting up Change Management in SAS Intelligence Platform: Desktop Application Adminstration Guide.Permission Tips for Selected Content and Data Objects
Permissions Tips: Selected Content and Data Objects
|
The root folder (the
SAS Folders node) is an important point of control for narrowing WM.
Unlike other folders, the root folder does not have the WriteMemberMetadata
permission in its permission list. This is because the root folder
is a software component object, not a true folder. The root folder
can contain only other folders.
|
|
|
For folders, follow
these guidelines:
|
|
|
To run a stored process,
you need ReadMetadata permission on the stored process. If you can
see a stored process but can't run it, you might lack the necessary
grant of Read permission for the underlying data. To register a stored
process, you need WriteMetadata permission for the target application
server.
The method that you
use to make a stored process available can affect data retrieval and
security. For example, in the standard configuration, a stored process
that is assigned to a workspace server and embedded in an information
map retrieves SAS data under the pooled workspace server's host identity.
However, if a user opens that same stored process directly (for example,
as a report in SAS Web Report Studio), the host identity of the requesting
user (or group) retrieves the data.
|
|
|
In a new deployment,
only the SAS Administrators group can add channels, subscribers, and
content. To enable all registered users to publish content to a particular
channel, navigate on the Folders tab to System
|
|
|
See Implementing Security for SAS BI Dashboard in SAS Intelligence Platform: Web Application Administration Guide. Dashboards and their related items (indicators, data models,
and ranges) have a specialized authorization model.
|
|
|
To register cubes, you
need WriteMetadata permission for the OLAP schema and WriteMemberMetadata
permission for the target folder. To associate a cube with a schema,
you need WriteMetadata permission for the cube and the schema.
|
|
|
For cube components,
Read permission is enforced. If you lack access to a measure that
participates in a calculated measure, you can get unintended results.
There are also navigational
requirements for Read permission on cube components. If a user does
not have Read permission to a hierarchy, the user can't navigate to
the top levels within the hierarchy. If a user does not have Read
permission to a particular level in a hierarchy, the user can't navigate
to the next level.
|
|
|
To associate a library
with an application server, you need WriteMetadata permission for
the server (but not for the library). For a library that is accessed
via the metadata LIBNAME engine (MLE), you need the Create permission
in order to add tables and the Delete permission in order to delete
tables.
|
|
|
To associate a table
with a library, you need WriteMetadata permission for the table and
the library. For a table that is accessed via the MLE, you need Read
permission in order to access data. The Create, Delete, and Write
permissions affect your ability to add, update, or delete data. You
can grant these permissions broadly (as described in the information
map row) or narrowly (for example, to a small group of users on a
particular table.
|
|
Permission Tips for Selected System and Administrative Objects
Permissions Tips: Selected System and Administrative Objects
|
To monitor or operate
servers other than the metadata server, you need the Administer permission
on the server. (The metadata server requires the Metadata
Server: Operation role instead of the Administer permission.)
To associate a stored
process, OLAP schema, or library with an application server, you need
WriteMetadata permission for that application server. Certain service
identities need ReadMetadata permission to all server definitions.
See Permissions on Servers.
|
|
|
To use a logical server,
you need ReadMetadata permission for at least one of that server's
connections. This is called server access security. Certain service
identities need ReadMetadata permission to logical server definitions. See Hide Server Definitions.
|
|
|
User administration
capabilities (from the Metadata Server: User Administration role)
enable you to create, update, and delete users, groups, and roles.
You can delegate management of an identity to someone who doesn't
have user administration capabilities by adding explicit or ACT
grants of WriteMetadata permission in the identity's authorization
properties. An identity's authorization properties have no effect
on what that identity can do.
|
|
|
To create an ACT, you
need repository-level WriteMetadata permission. Each predefined
ACT is protected by direct access controls. ACTs that you create aren't
automatically protected. It is essential to add protections (direct
controls in the ACT’s authorization properties) to any ACTs
that you create.
|