Security and BI Row-Level Permissions
Introduction
Like any other security feature, a secure implementation
of BI row-level permissions requires that you pay careful attention
to the entire environment in order to avoid vulnerabilities in other
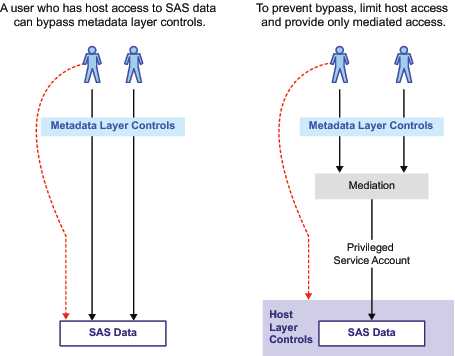
security layers. For example, if you do not limit physical access
to the target data, there is a risk that users will exploit their
physical access to circumvent the filters that you define in your
information maps. If this is an acceptable risk, then no special measures
are needed. This can be an acceptable risk in environments such as
the following:
If, on the other hand,
you require strict security controls against the possibility of malicious
activity on your company intranet, then a more tightly protected configuration
is necessary. In such circumstances, it is important to strictly limit
physical access to the target tables to prevent direct access by regular
users. The goal is to enable regular users to have only mediated access
to the target tables. The strategy is as follows:
The Initial Configuration
The initial configuration
in a new deployment uses mediated access for BI row-level permissions.
The server-side pooled workspace server is used for queries against
relational information maps. The following figure depicts this mediation
of physical access.
In the initial configuration, mediation is achieved through
server-side workspace server pooling. The server’s launch credential
retrieves data for all requesting users. The server’s launch
credential must have physical access to the data. End-users don’t
need physical access to the data. This mediation, in combination with
appropriate physical layer access controls, provides some separation,
because it prevents users from directly accessing the data under their
own credentials.
Incremental Measures for Increased Protection
There are several options for incrementally reducing
the likelihood of inappropriate access. For example:
Neither of these options provides comprehensive security,
because it is possible for a sophisticated end user to exploit a server-side
pooled workspace server and obtain direct (unfiltered) access to the
data. For this reason, the secure environment uses a client-side pooled
workspace server, instead of a server-side pooled workspace server.
About the Secure Environment
Overview of the Secure Environment
Here are the key
points of the configuration:
-
You create an additional deployment instance of SAS Web Report Studio. The pool administrator account is known to only the new deployment instance of SAS Web Report Studio, so no other applications can use the pool (and, potentially, exploit the puddle login credential).Note: In the secure configuration, the only supported client for presenting reports to end users is SAS Web Report Studio. The sensitive data is not available from other applications, such as SAS Enterprise Guide, because physical layer protections grant access to only the puddle account, which is known only to SAS Web Report Studio.